For businesses in Phoenix, Arizona, ignoring secure hard drive disposal isn't just a compliance oversight; it's a gaping hole in your company's security. This is about more than just deleting files. It’s about using certified, irreversible methods to make sure your data is gone for good.
This process protects your Phoenix-based business from breaches, keeps you on the right side of laws like GDPR and HIPAA, and protects your reputation. Honestly, treating data destruction as a core part of your operations is the single best investment you can make to protect your company's most valuable asset—its data.
The High Stakes of Improper Disposal
Forgetting about an old hard drive is one of the easiest—and most common—ways to create a massive business vulnerability. A single discarded drive can be a goldmine of sensitive information, holding everything from customer lists and financial records to intellectual property and employee PII (Personally Identifiable Information). In the wrong hands, that data is a weapon.
The consequences aren't just theoretical. Failing to have a secure disposal strategy in place can hit your business from multiple angles, and many companies have learned this the hard way.
Financial and Legal Ramifications
Regulators don't mess around with data privacy. Laws like the Health Insurance Portability and Accountability Act (HIPAA), the General Data Protection Regulation (GDPR), and the California Consumer Privacy Act (CCPA) have sharp teeth and come with strict rules for handling and destroying sensitive data.
A breach from an improperly disposed drive can trigger devastating fines. Just look at Morgan Stanley—they were fined a staggering $35 million by the SEC for failing to properly decommission thousands of hard drives. Those drives held the PII of about 15 million customers. This wasn't a complex cyberattack; it was a simple failure in their IT asset disposal process. Penalties like that can wreck a company's finances and bog it down in legal battles for years.
The infographic below shows exactly how a preventable mistake can lead to massive fines and lasting brand damage.
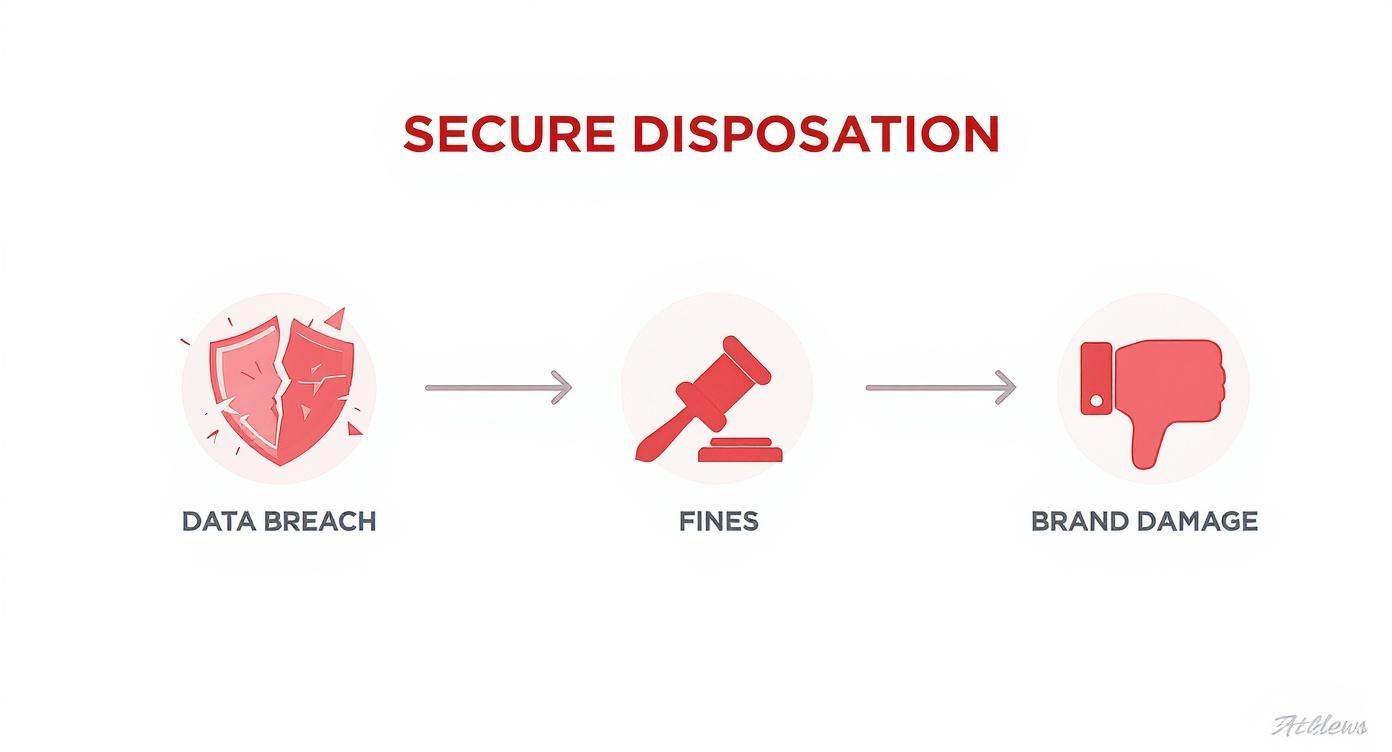
As you can see, it's a straight line from a simple oversight to significant financial and reputational fallout.
Irreversible Brand and Reputational Damage
As bad as the financial hit is, the damage to your company's reputation can be far worse and last much longer. Trust is everything in business, and a data breach destroys it in an instant.
"A data breach is not just a loss of data; it's a loss of customer confidence. Rebuilding that trust is exponentially harder and more expensive than protecting the data in the first place."
News of a breach spreads like wildfire. You're looking at negative press, angry customers leaving in droves, and a tarnished public image that could take years to fix—if you can fix it at all. Future clients will think twice before working with a company known for mismanaging data. A great way to build a comprehensive defense is to pair secure disposal with a broader understanding of security program management.
From Afterthought to Operational Priority
Treating hard drive disposal like a janitorial task is a huge strategic mistake. It needs to be woven directly into your company's risk management and data security framework. It’s time to stop reacting and start being proactive.
A formal IT Asset Disposition (ITAD) policy shouldn't be something you scramble to create during an equipment refresh; it needs to be standard procedure. This policy should clearly define:
- Clear Procedures: Lay out the exact steps for handling retired assets, from inventory tracking all the way to final destruction.
- Vendor Vetting: Have set criteria for choosing a certified ITAD partner who provides auditable proof that your drives have been destroyed.
- Chain of Custody: Implement a documented trail that tracks every single asset from the moment it leaves your building until its destruction is confirmed.
By making secure disposal a non-negotiable part of your workflow, you turn a major liability into a protected, controlled process. There are so many crucial reasons you need data destruction services today, and getting this right is essential for protecting your organization long-term.
Data Wiping vs. Physical Destruction: Which Is Right for Your Business?

When it's time to retire old IT assets, the big question is always how to handle the data left on them. The decision really comes down to two paths: using software to wipe the drives clean or physically destroying them completely. This isn't just a technical choice—it's a strategic one that hits your security, your budget, and whether you can get any value back from that old equipment.
Each approach has its place. Knowing the real-world differences is the key to making sure your disposal strategy lines up with your company's security policies and financial goals.
The Case for Data Wiping and Sanitization
Data wiping, or what professionals call sanitization, involves using special software to completely overwrite the data on a hard drive with random characters. This isn't a one-and-done process; it’s repeated multiple times to make absolutely certain the original information is gone for good and can't be recovered with any forensic tools.
The whole process is guided by tough industry standards, with the NIST 800-88 Guidelines for Media Sanitization being the gold standard. When done right, data wiping makes data retrieval impossible. We take this standard seriously, and you can get the full rundown in our complete guide to NIST SP 800-88 media sanitization.
The main perk of wiping is that the hard drive itself remains perfectly usable. This makes it the go-to choice for businesses looking to:
- Remarket and Resell Assets: If your IT gear still has some life left in it, wiping lets you sell it and recoup some of your initial investment.
- Redeploy Devices Internally: A securely wiped device can be safely passed on to another employee or department within your organization.
- Donate Equipment: Wiped computers can be donated to schools or non-profits, which is great for corporate social responsibility without creating a data risk.
A common mistake is thinking that a simple "format" or just deleting files gets the job done. Those actions only remove the pointers to your data, leaving the actual information sitting there, ready to be recovered. Professional data wiping is the only software method that guarantees permanent removal.
But wiping isn’t a perfect fit for every situation. It needs the hardware to be in working order and can be slow, especially when you have a mountain of drives to get through. For drives that are broken or too old to have any resale value, physical destruction is often the smarter, more secure route.
When Physical Destruction Is Non-Negotiable
Physical destruction is exactly what it sounds like—the complete and total annihilation of the hard drive. This method ensures that the drive and every last bit of data it held are gone forever, with zero chance of recovery. It’s the final word in data security for any media at the end of its life.
The need for this level of security is massive. The global data destruction service market is already valued at USD 12 billion and is expected to rocket to USD 39.3 billion as companies face down growing data volumes and tighter regulations.
There are a couple of primary ways professionals handle physical destruction:
- Degaussing: This technique uses an incredibly powerful magnetic field to instantly wipe the magnetic data from traditional hard disk drives (HDDs). It’s fast and effective, but there's a huge catch: it does not work on Solid-State Drives (SSDs), which store data on flash memory chips, not magnetic platters.
- Shredding: This is the most secure and universally effective option. Industrial shredders take hard drives—both HDDs and SSDs—and grind them into tiny, unrecognizable pieces of metal. It's final, easily verifiable, and leaves no room for doubt.
Making the Right Business Decision
So, wiping or shredding? Your choice really hinges on your specific situation. Think about these key factors:
- Asset Value: Do the hard drives or the devices they're in have any resale or reuse value? If so, wiping is your best bet. If not, physical destruction is faster and more efficient.
- Drive Type: What are you dealing with? A mix of HDDs and SSDs? Remember, degaussing only works on HDDs, while shredding handles everything.
- Security Policy: Does your company policy or a regulatory requirement (like HIPAA or government contracts) demand physical destruction? In that case, the decision is already made for you.
- Volume and Time: How many drives do you need to process? Wiping can be a slow grind for large quantities, making on-site shredding a much quicker solution for bulk disposals.
Comparing Data Destruction Methods
To make it even clearer, here’s a quick breakdown of how these methods stack up against each other.
| Method | Security Level | Drive Reusability | Best For | Verification |
|---|---|---|---|---|
| Software Wiping | High (NIST 800-88) | Yes, fully reusable | Reselling, redeploying, or donating valuable IT assets. | Digital log files and reports confirm successful overwrites. |
| Degaussing | Very High (for HDDs) | No, drive is rendered inoperable | High-security disposal of traditional magnetic hard drives (HDDs). | Visual inspection and checking for loss of magnetic field. |
| Physical Shredding | Highest Possible | No, completely destroyed | End-of-life, damaged, or SSD media; meeting strict compliance mandates. | Certificate of Destruction, visual confirmation of shredded particles. |
Ultimately, whether you choose to wipe or destroy, the goal is the same: ensuring your sensitive data doesn't fall into the wrong hands. By weighing the value of your assets against your security requirements, you can build a disposal plan that is both responsible and financially sound.
Mastering the Chain of Custody for IT Assets

Secure hard drive disposal isn't just a one-and-done event; it's a documented, auditable process from start to finish. This is where a solid chain of custody (CoC) becomes your most important line of defense. It provides an unbroken, verifiable trail for every single asset, from the moment it leaves your building to its final destruction.
Without a detailed CoC, you're essentially creating a black hole of liability. If a drive vanishes or data gets compromised after it’s off your property, the lack of a paper trail makes it nearly impossible to prove you did your part. A strong CoC isn’t just about logistics—it’s about transferring risk and proving due diligence.
What a Rock-Solid CoC Looks Like in Practice
A truly secure chain of custody is a series of clearly defined, documented steps that leave no room for error. The process actually begins long before a truck ever shows up at your door.
It should always start with thorough inventory management on your end. This means creating a serialized asset list that uniquely identifies every hard drive or device you’re getting rid of. Each item gets tagged and scanned, creating a manifest that becomes the foundational document for the entire process. This initial inventory is the baseline that everything else is checked against.
The handover process is critical. When your ITAD partner arrives, their team should verify your manifest by scanning each asset tag to confirm the inventory is an exact match. This documented reconciliation is the first formal transfer point in the chain of custody.
Secure Transport and Facility Reconciliation
Once the assets are loaded into a locked, GPS-tracked vehicle, the chain of custody continues. The transport phase is a potential weak link, which is why working with a certified partner who uses their own vetted employees and secure vehicles is so important.
The process repeats upon arrival at the secure ITAD facility. The sealed vehicle is opened, and the assets are unloaded into a restricted-access area, often under video surveillance. The manifest is checked yet again, with every single asset scanned to confirm that what left your facility is exactly what arrived at theirs. Any discrepancy, no matter how small, has to be investigated and reconciled immediately.
A proper chain of custody ensures that at every point—from your loading dock to the shredder—there is a clear, documented record of who had possession of your assets and when. This transparency is the cornerstone of regulatory compliance and risk mitigation.
The Final Documentation Proving Compliance
The chain of custody isn't complete until you have the final documentation that formally closes the loop on your liability. This isn't just extra paperwork; it’s your legal proof of proper disposal.
The most important document you’ll receive is the Certificate of Destruction (CoD). This is a legally binding document that details everything:
- A unique serial number for the certificate itself
- The date and location of the destruction
- The specific method used (e.g., shredding, pulverizing)
- A finalized, serialized list of all destroyed assets, cross-referenced against the original manifest
This certificate formally transfers the liability for the data from your organization to the ITAD vendor. It serves as your undeniable proof if you ever face an audit from regulatory bodies enforcing rules like HIPAA or GDPR. You can learn more about why this document is so vital by reviewing our guide on the importance of a Certificate of Destruction. Without it, you're leaving your organization exposed to serious legal and financial risk long after your assets are gone.
How to Vet and Choose a Certified ITAD Partner

Choosing a partner for secure hard drive disposal is a critical decision for any Phoenix business. You're not just hiring a vendor; you're trusting them with your company's sensitive data. Think of them as an extension of your security team, because a bad choice can expose you to the exact risks you’re trying to prevent.
Not all data destruction vendors are the same, and picking the right one goes way beyond a simple price comparison.
A real IT Asset Disposition (ITAD) partner does more than just shred your drives. They shield you from future liability with a process that's transparent, certified, and completely auditable. You can learn more about the fundamentals in our overview of what IT Asset Disposition is. Knowing what to look for is everything.
Decoding Key Industry Certifications
Certifications are your first line of defense against irresponsible vendors. They’re independent proof that a partner meets high standards for data security, environmental practices, and employee safety.
When you're looking at potential partners, keep an eye out for these big three:
-
R2 (Responsible Recycling): The R2 Standard covers the entire ITAD lifecycle, from data wiping and testing to making sure materials are recovered properly. An R2-certified facility has passed audits proving it follows best practices for protecting the environment and its workers.
-
e-Stewards: This is another major global standard for responsible e-recycling. The e-Stewards certification is especially known for its strict ban on exporting hazardous e-waste to developing nations.
-
NAID AAA: This one is laser-focused on data destruction. The National Association for Information Destruction (NAID) AAA Certification is non-negotiable. It confirms that a vendor's hiring, security, and destruction processes meet tough, closed-loop standards designed to protect confidential information.
These aren't just logos they slap on a website; they represent a serious, ongoing investment in doing things the right way.
Essential Questions for Every Potential Vendor
Once you've confirmed a vendor has the right certifications, it's time to dig into their actual process. A reputable partner will be happy to answer your questions and give you clear, detailed information.
Your vetting process should be thorough. Use the following checklist as a guide to make sure you don't miss anything important.
If a vendor hesitates or can't give you clear, documented answers about their security, insurance, or downstream partners, that's a major red flag. When your company's data is on the line, transparency is everything.
The need for professional services has made this market grow fast. The global hard drive shredding services market was valued at USD 0.72 billion and is expected to hit USD 1.2 billion, which shows just how vital these services are, especially for regulated industries.
Your Vendor Vetting Checklist
Go into your conversations armed with these questions to confidently evaluate any potential ITAD partner.
Security and Personnel
- Are all your employees who handle our assets background-checked and drug-screened?
- What are your facility's security protocols? Tell me about access control and video surveillance.
- Do you use your own employees and trucks for transport, or do you subcontract that out?
Processes and Documentation
- Can you show me a detailed, serialized chain-of-custody report for every asset?
- What information is on your standard Certificate of Destruction? Can I see a sample?
- Do you offer on-site destruction? What does that process look like?
Insurance and Liability
- What kind of liability insurance do you carry, and what are the coverage amounts? Be sure to ask about pollution liability and errors and omissions coverage.
- Can you provide a certificate of insurance that names our company as additionally insured?
Downstream and Environmental
- Who are your downstream recycling partners? Are they certified, too?
- Can you give us a full downstream map showing where every piece of material ends up?
- What percentage of the material you handle is recycled versus landfilled? (Hint: For a certified recycler, the answer for focused material should be 0%).
Picking the right ITAD partner is about finding a company that is as serious about security and compliance as you are. A deep vetting process ensures your hard drive disposal plan is built on a foundation of trust and proven expertise.
On-Site vs. Off-Site Destruction: What to Consider
Deciding between on-site and off-site hard drive destruction is a critical balancing act. You're weighing maximum security against operational convenience and cost. Both methods get you to the same end goal—complete data annihilation—but the journey is quite different. The right choice really comes down to your company's risk tolerance, compliance requirements, and logistics.
Let’s break down the practical differences. On-site destruction brings the entire process right to your doorstep, while off-site services handle everything at a secure, specialized facility.
The Case for On-Site Destruction
For many organizations, especially those in highly regulated fields like finance, healthcare, or government, on-site destruction is simply non-negotiable. The primary advantage is undeniable: complete transparency. You can physically witness your hard drives being turned into tiny metal fragments, giving you irrefutable proof that the data is gone before it ever leaves your property.
This hands-on approach offers some key benefits:
- Immediate Verification: There is zero gap in the chain of custody. You watch the destruction happen in real-time and can get a Certificate of Destruction right on the spot.
- Eliminates Transit Risk: The risk of data exposure during transport, while minimal with a certified vendor, is completely removed from the equation.
- Ultimate Peace of Mind: For IT managers and compliance officers, being able to personally oversee the process provides the highest level of assurance possible.
Picture a hospital decommissioning servers that hold patient health information (PHI). The potential penalties for a HIPAA violation are massive. By opting for on-site shredding, the hospital's compliance officer can supervise the entire event, document it, and immediately secure the paperwork needed for their audit trail. That level of control is often worth the premium cost of bringing a mobile shredding truck to their location.
When Off-Site Destruction Makes Sense
While on-site destruction offers maximum visibility, don't discount off-site services. They bring significant advantages in cost-effectiveness and convenience, particularly for large-scale projects. If your business is tackling a major IT refresh or decommissioning a data center with hundreds or even thousands of assets, the logistics of shredding everything on-site can be disruptive and incredibly time-consuming.
When managed by a certified ITAD partner, off-site destruction is just as secure. The process hinges on a rigorous, documented chain of custody. Think locked and sealed transport containers, GPS-tracked vehicles, and facilities with intense security protocols.
This option is often the best fit for:
- Large Volume Projects: It's just far more efficient to process thousands of drives in a dedicated facility built for high-volume shredding.
- Cost-Sensitive Operations: Off-site services are typically more affordable. The vendor can streamline their operations without the overhead of mobile equipment and travel time.
- Minimal Business Disruption: Your team isn't tied up for hours watching a shredder. The assets are securely removed, and you receive the Certificate of Destruction once the job is completed at the vendor’s facility.
The global market for hard disk destruction equipment was valued at USD 2.85 billion and is projected to hit USD 3.75 billion, a clear sign of the growing demand for professional solutions. This growth is directly tied to the need for businesses to comply with data protection laws like GDPR and CCPA, whether they choose on-site or off-site methods. If you're looking to explore local options, Beyond Surplus provides a comprehensive hard drive shredding service near you that can handle either preference.
Ultimately, the decision isn't about which method is "better." It's about which one aligns best with your organization's specific security framework and operational needs. A trusted partner will offer both and help you figure out the most appropriate strategy.
By carefully evaluating the trade-offs between visibility, cost, and logistics, you can confidently pick a hard drive disposal method that protects your data and keeps you compliant.
Answering Your Secure Hard Drive Disposal Questions
When you're putting together a plan for secure hard drive disposal, a lot of specific questions tend to pop up. It's one thing to have a strategy, but navigating the real-world details—like choosing between destruction methods and meeting compliance rules—is where things get tricky. Let's walk through some of the most common questions we hear from businesses, so you can make the right calls and keep your organization safe.
Is Degaussing Enough for Secure Hard Drive Disposal?
Degaussing is an incredibly powerful way to sanitize traditional magnetic hard disk drives (HDDs). It hits them with a massive magnetic field that completely scrambles the data on the platters, making it impossible to recover. For HDDs, it’s a slam dunk.
But here’s the catch: that method is completely useless on Solid-State Drives (SSDs). SSDs don't store data magnetically; they use flash memory chips that a degausser can't touch. If you're dealing with a mix of drives and you only degauss them, you're leaving a massive security hole wide open. For this reason, physical destruction like shredding is the only method that guarantees security across all modern drive types.
What Is a Certificate of Destruction and Why Do I Need It?
A Certificate of Destruction (CoD) isn't just a receipt. Think of it as your official, legally-defensible proof that your data-bearing assets were destroyed correctly and according to industry standards. For any business that has to comply with data privacy laws like HIPAA, GDPR, or the FTC Disposal Rule, this document is non-negotiable.
A legitimate CoD from a certified ITAD partner should always include:
- A unique serial number for easy tracking
- The exact date, time, and location of destruction
- The specific method used (e.g., shredding to a 5mm particle size)
- A serialized list of every single asset that was destroyed
- A formal statement confirming the transfer of liability
Bottom line: if you ever face an audit or a legal challenge, the Certificate of Destruction is your ironclad proof of due diligence. It shows you took all the necessary steps to protect sensitive data and formally shifts the liability from your shoulders to your disposal partner.
Can We Just Drill Holes in Our Hard Drives Internally?
Drilling holes in a stack of old hard drives might feel productive, but from a business security standpoint, it’s a dangerously flawed DIY approach. Forensic experts can still pull a surprising amount of data from the parts of the platters that weren't hit by the drill bit. A single hole leaves most of the data-storing surfaces perfectly intact.
Even more critical, this method leaves you with zero auditable trail for compliance. There's no verifiable proof of destruction, no chain of custody, and certainly no Certificate of Destruction. For any company subject to data protection laws, manual methods like drilling or hammering create an unacceptable level of risk and simply don't meet legal muster.
What Happens to the Shredded Hard Drive Material?
After your hard drives are turned into tiny, confetti-like pieces of metal, they don’t just get dumped in a landfill. A certified ITAD partner is committed to handling that material responsibly. The shredded mix of aluminum, steel, and electronic components is securely transported to a specialized downstream refinery.
There, a sophisticated process separates all the different materials. Valuable commodities like aluminum, steel, copper, and even trace amounts of precious metals are recovered and put back into the manufacturing supply chain. This doesn't just comply with environmental regulations like the RCRA—it also helps your company meet its own sustainability goals by contributing to a circular economy.
When it's time to ensure your company's data is destroyed securely and responsibly, trust the experts. Beyond Surplus provides certified electronics recycling and secure IT asset disposal services for businesses in Phoenix and across the United States. For a consultation on your secure disposal needs, visit us at https://www.beyondsurplus.com.



