For enterprise organizations, "technology reuse" is a strategic approach to IT Asset Disposition (ITAD) that transforms retired equipment into a significant business advantage. For businesses across Georgia, this means a secure, documented process of wiping data, remarketing viable assets for value recovery, and responsibly recycling end-of-life electronics. This methodology integrates IT governance, financial optimization, and corporate social responsibility into a single, efficient workflow.
Why Technology Reuse Is a Strategic Imperative for Georgia Businesses

From Atlanta's dynamic tech corridors to Savannah's critical logistics hubs, the management of retired IT assets has evolved. The outdated "store it or scrap it" approach is no longer viable for commercial enterprises, given today’s stringent data security regulations and environmental standards. A professional technology reuse program addresses two core business challenges simultaneously: mitigating the significant risk of data breaches and unlocking the residual financial value in used IT hardware. By prioritizing reuse, companies protect their brand reputation, ensure compliance, and generate a return on their initial technology investment.
Core Pillars of a Reuse Strategy
An effective technology reuse program for your business is built on four key pillars, each delivering measurable benefits.
-
Data Security and Compliance: The primary objective is the complete elimination of data security risks. Certified data destruction guarantees that all sensitive corporate and customer information on hard drives and storage media is irretrievably destroyed, providing a complete audit trail for compliance with regulations like HIPAA and FACTA.
-
Value Recovery: Not all retired equipment is obsolete. Enterprise-grade servers, networking equipment, and corporate laptops often retain significant value on the secondary market. A professional ITAD partner will test, grade, and remarket these assets, converting a disposal cost center into a new revenue stream.
-
Environmental Responsibility: Reuse is the most effective form of recycling. Extending the operational life of IT assets drastically reduces their environmental footprint, conserves valuable natural resources, and helps your company achieve its corporate sustainability goals. Learn more about professional IT equipment recycling in Georgia.
-
Operational Efficiency: A streamlined and professionally managed disposition process frees up valuable corporate real estate and internal IT resources. This allows your team to focus on core business functions that drive growth, rather than managing obsolete hardware.
Georgia's Growing Role in the Circular Economy
Georgia has established itself as a key player in the circular economy, an economic model focused on eliminating waste through the continuous reuse of resources. This is not merely an environmental objective; it is a powerful economic shift creating tangible opportunities for businesses across the state. The infrastructure supporting advanced technology reuse in Georgia is expanding rapidly.
When your company engages a local, certified ITAD provider, the positive impact extends beyond your balance sheet. IT directors and facility managers can align their asset disposal strategies with statewide economic and environmental objectives. Partnering with a Georgia-based firm supports local job growth, contributes to state sustainability targets, and enhances your company's reputation as a responsible corporate citizen.
State-Level Investment in a Greener Future
Georgia's commitment to the circular economy is evident in significant statewide investments. The state is becoming a hub for advanced recycling, with 10 major projects announced in a single year, bringing in over $1.8 billion in investments. A prime example of this momentum is Igneo Technologies' $85 million electronics recycling facility in Savannah.
This state-of-the-art plant is engineered to extract valuable, reusable metals from e-waste, directly addressing the global challenge where only 17.4% of electronic waste is properly collected and recycled. Such investments create a robust local ecosystem for managing retired electronics, making it simpler for Georgia businesses to adopt responsible practices. You can read about Georgia's advanced recycling initiatives to understand the full scope.
This large-scale development directly supports your company’s needs by providing the heavy-duty infrastructure required to ensure your retired IT assets are managed ethically, securely, and with maximum value recovery.
The Practical Impact on Your Business
What does this statewide focus on technology reuse mean for your day-to-day operations? It means your business has access to a sophisticated network of local experts who can convert a compliance burden into a strategic advantage.
Instead of viewing old laptops, servers, and networking gear as liabilities, you can see them as components in a value chain. A professional ITAD partner in Georgia can help your business:
- Ensure compliance with all data privacy regulations through certified data destruction.
- Recover financial value from assets with remaining market viability.
- Achieve sustainability goals by extending the life of electronic equipment.
- Strengthen brand image through a clear, demonstrable commitment to environmental responsibility.
These state initiatives provide the foundation for your business to implement a secure, profitable, and responsible asset disposition program. To learn more, see how to mitigate the environmental impact of electronic waste with certified partners. This proactive approach not only protects your organization but also solidifies its role in Georgia's thriving circular economy.
How the IT Asset Disposition Process Works
For many IT managers in Georgia, the process after equipment is scheduled for pickup can seem opaque. A professional IT Asset Disposition (ITAD) process is not a mystery; it is a secure, fully documented "reverse supply chain" designed to protect your organization at every stage.
The process begins when your technology assets are designated for removal. A certified ITAD partner dispatches its own background-checked technicians in secure, company-owned vehicles to manage the logistics of your project, whether it involves a few pallets of laptops or a complete data center decommissioning.
Establishing a Secure Chain of Custody
From the outset, the most critical element is establishing an unbroken chain of custody. This is the documented audit trail that tracks every single asset from the moment it leaves your facility until its final disposition.
- On-Site Inventory: Technicians create a detailed inventory at your location, often by scanning serial numbers, to ensure every piece of equipment is accounted for before transport.
- Secure Transport: Your assets are loaded into locked containers and transported directly to the secure processing facility, eliminating risky third-party handoffs that could create security vulnerabilities.
- Facility Check-In: Upon arrival, the sealed containers are opened, and the inventory is reconciled against the original on-site list to confirm that all assets arrived securely and without tampering.
This meticulous tracking provides a transparent and defensible record essential for compliance and corporate governance. To see how this fits into the bigger picture, check out our guide on what IT asset disposition is.
Data Destruction and Asset Evaluation
Once assets are secured within the facility, the process shifts to two key functions: destroying all data and determining the equipment's value. This is where a partner’s certifications, such as R2 or e-Stewards, become critical. These credentials mandate the strict operational standards that must be followed.
Data destruction is always the first priority. Any device capable of storing data undergoes a certified data sanitization process based on NIST 800-88 guidelines, ensuring all data is completely and permanently erased. Drives that fail sanitization or are outdated are physically shredded.
Following data destruction, you receive a formal Certificate of Data Destruction. This legal document serves as your proof of compliance and officially transfers liability from your company to the ITAD vendor.
With data security confirmed, each asset is tested and graded. Technicians evaluate its condition, specifications, and potential for reuse. This assessment determines whether a device can be refurbished and remarketed to recover value for your business or if it requires responsible recycling. This dual approach ensures maximum security and the best possible financial return—the core of effective technology reuse in Georgia.
Protecting Your Business with Certified Data Destruction
When retiring IT assets, data security is the paramount concern. For any business in Georgia, a failure to protect sensitive information represents a significant liability, carrying the risk of severe financial penalties and irreparable brand damage.
This is why certified data destruction is a non-negotiable component of any responsible technology reuse program. It is the critical step that ensures your company remains compliant with stringent data privacy laws governing corporate, customer, and employee information.
Meeting Critical Compliance Standards
Several federal laws mandate the secure disposal of data, and non-compliance can be exceptionally costly. Certified data destruction is your primary defense in meeting these legal requirements.
- HIPAA (Health Insurance Portability and Accountability Act): For organizations in the healthcare sector, HIPAA requires that all patient health information is rendered completely unreadable and irrecoverable before any electronic device is discarded.
- FACTA (Fair and Accurate Credit Transactions Act): This law applies to nearly all businesses and requires the secure destruction of consumer information to prevent identity theft.
- FTC Disposal Rule: This rule mandates that businesses take "reasonable measures" to protect against unauthorized access to consumer information during its disposal.
A certified process provides the necessary documentation to prove due diligence and satisfy any audit requirements.
This infographic illustrates the essential steps of a secure IT asset disposition process, from initial pickup to final reporting.
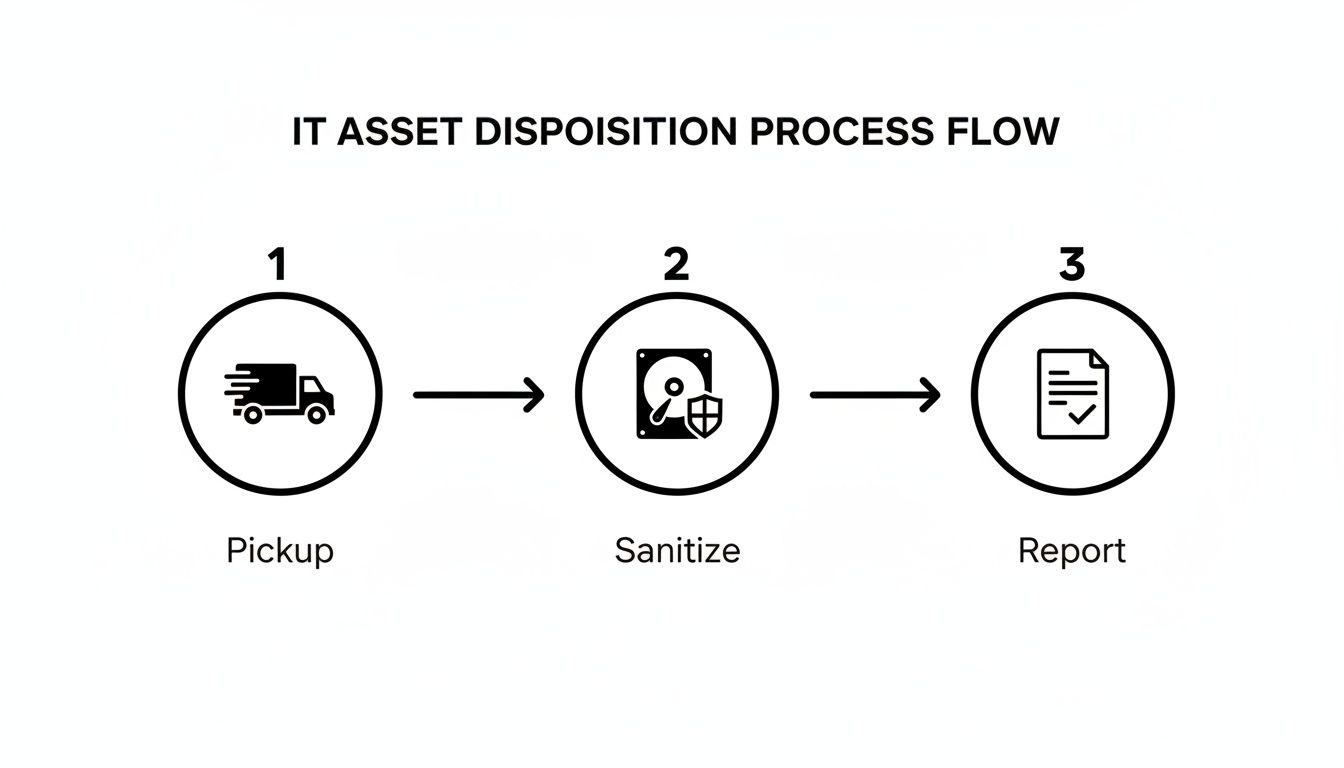
As shown, a compliant process is a closed loop where security and documentation are maintained at every stage.
Sanitization vs. Physical Destruction
The appropriate data destruction method depends on your internal security policies and the media type. The two primary, compliant approaches are data sanitization and physical destruction.
Data sanitization (data wiping) uses specialized software to overwrite all existing data on a hard drive according to strict standards like NIST 800-88, ensuring no data is recoverable. This method leaves the physical drive intact, enabling its reuse or resale, which is ideal for value recovery programs.
Physical destruction involves shredding the hard drive or storage device into small fragments, making data recovery impossible. This is the preferred method for damaged drives or for companies with policies requiring the complete physical destruction of all storage media.
Beyond Surplus can help determine and execute the best approach for your business. Learn more about our comprehensive data security services in Georgia.
The most critical document you will receive is the Certificate of Data Destruction. This legal document lists every serialized asset that was sanitized or destroyed, officially transfers liability from your business to your ITAD partner, and provides a solid, defensible record for any future audits.
Turning Retired IT Hardware into Revenue
A strategic approach to technology reuse in Georgia extends beyond compliance to deliver significant financial benefits. Many businesses view retired IT equipment as a sunk cost or an operational burden, overlooking a substantial opportunity for IT Asset Value Recovery (ITAVR). It is time to shift from seeing old tech as a liability to recognizing it as a tangible asset.
This process is a deliberate strategy of identifying, refurbishing, and remarketing equipment that retains value in the secondary market. Think of it as managing a technology portfolio; just as you would not discard valuable financial assets, you should not discard valuable hardware.
Identifying High-Value Assets
Not all retired equipment is equal in value. Certain categories of hardware consistently retain value and are prime candidates for remarketing. An experienced ITAD partner can identify these assets and maximize your return.
High-value equipment categories often include:
- Enterprise Servers and Networking Gear: Components from brands like Cisco, Dell, and HP remain in high demand for parts or for deployment in smaller business environments.
- Recent-Model Laptops and Desktops: Business-class laptops, particularly those less than five years old, are highly sought-after for refurbishment.
- Specialized Medical or Laboratory Equipment: While a niche market, functional and properly decommissioned devices can command high resale prices.
The global e-waste stream contains significant value. In a recent year, 53.6 million tons of e-waste contained raw materials worth an estimated $57 billion. A staggering $47 billion of this value—from metals like gold, silver, and copper—was lost due to inadequate recycling and reuse programs. You can explore the value hidden in e-waste on grandviewresearch.com.
The Financial Benefits of ITAVR
Implementing a formal asset recovery program delivers direct financial gains that can offset IT budget expenditures. Revenue generated from the sale of refurbished equipment can cover the costs of data destruction and recycling for non-value assets.
A well-managed ITAVR program can often be cost-neutral or even generate a net positive return. This transforms your ITAD process from a necessary expense into a self-funding or profitable business function.
This financial upside is central to modern technology reuse. By partnering with a specialist who understands the secondary market, Georgia businesses can capture the maximum value from their retired assets. Learn more about how we can help by exploring our asset recovery services in Georgia. This approach aligns financial goals with environmental commitments.
How to Choose the Right ITAD Partner in Georgia
Selecting the right IT Asset Disposition (ITAD) partner is the most critical decision in your technology reuse strategy. This is not merely contracting a hauler for old equipment; you are entrusting a vendor with your company's sensitive data, valuable hardware, and legal compliance. A misstep can lead to a data breach, environmental fines, or significant reputational damage.
To protect your business, you need a partner who operates with complete transparency, robust security, and proven expertise. This requires looking beyond price quotes to scrutinize a vendor’s certifications, processes, and physical capabilities within Georgia. A true ITAD specialist provides a fundamentally different service than a general scrap recycler, prioritizing security and value recovery above all else.
Key Certifications to Look For
Industry certifications are non-negotiable. They serve as an independent, third-party guarantee that a vendor adheres to the highest standards for data security, environmental responsibility, and occupational health and safety.
- R2 (Responsible Recycling): This certification validates that the provider follows best practices for electronics recycling, with a strong emphasis on environmental protection and data security.
- e-Stewards: Often considered the most stringent standard, e-Stewards certification ensures that no hazardous e-waste is exported to developing nations and that all data is managed with the utmost security.
Your first question to any potential partner should be about their certification status. A lack of these credentials is a major red flag, indicating their processes have not been audited or verified to protect your interests.
When vetting a partner for technology reuse in Georgia, always request to see their certifications. A certified provider will readily share this documentation, giving you confidence that your assets are being managed responsibly from the moment they leave your facility.
Differentiating Specialists from General Recyclers
It is crucial to understand the difference between a specialized ITAD firm and a scrap metal recycler that also accepts electronics. A general recycler's business model is based on recovering raw materials by weight; their processes are not designed to manage data security risks or maximize the resale value of intact IT hardware.
In contrast, an ITAD specialist builds their entire operation around secure logistics, certified data destruction, and strategic asset remarketing. They use their own trained technicians and secure vehicles, provide detailed chain-of-custody documentation, and leverage deep knowledge of the secondary market to deliver the best possible return on your investment.
Choosing a partner with a dedicated physical presence and logistics team in Georgia adds a critical layer of accountability, ensuring your valuable assets are never handed off to unvetted third-party contractors.
Common Questions About Technology Reuse
Georgia businesses often have several key questions when managing retired IT assets. Here are clear answers to help you make informed decisions for your company.
What Is the Difference Between Technology Reuse and Electronics Recycling?
Technology reuse focuses on extending the life of equipment. It is a value-driven approach where viable assets are securely refurbished and resold. This should always be the primary consideration in your ITAD strategy.
Electronics recycling is the end-of-life process for non-functional items. It involves de-manufacturing equipment to recover raw materials. A responsible ITAD strategy prioritizes reuse before resorting to recycling.
Can You Handle Our Company's Specialized or Proprietary Equipment?
Yes. A full-service ITAD partner possesses the expertise to manage specialized assets from various sectors, including medical laboratories, data centers, and manufacturing facilities.
For proprietary technology, services like certified product destruction ensure your intellectual property is completely and irreversibly destroyed. This guarantees your technology will not appear on the secondary market, protecting your trade secrets and brand integrity.
How Is Our Data Kept Secure During Pickup and Transport?
Security begins at your facility, not at the processing plant. A reputable ITAD partner uses only their own trained, background-checked employees and a dedicated fleet of secure vehicles for all pickups.
Your assets are inventoried and sealed in locked containers on-site. From that point, a continuous chain-of-custody document tracks everything until it arrives at the secure processing facility. This closed-loop system is designed to eliminate security gaps.
Contact Beyond Surplus for certified electronics recycling and secure IT asset disposal. We provide certified, secure, and transparent ITAD services designed to protect your data, ensure compliance, and maximize your financial return. Schedule your business pickup today at https://www.beyondsurplus.com.



