When a U.S. business retires an old hard drive, it's like decommissioning a detailed company ledger. Simply hitting 'delete' on a file is like ripping an entry out of the table of contents—the actual information remains on the page, waiting for anyone with the right tools to find it. This creates a dangerous false sense of security for companies across the United States managing the disposal of old IT assets. For any business, understanding the nuances of secure hard drive destruction is not just an IT task; it's a critical component of corporate risk management and a legal necessity under U.S. data privacy laws.
Why Data Lingers on Your Old Corporate Hard Drives
When your business upgrades its technology, the old hard drives from computers, servers, and other enterprise equipment become a massive liability. These retired devices often hold years of sensitive information, from financial records and client data to your most valuable intellectual property. Improper disposal isn't a minor slip-up; it's a direct path to a data breach with staggering consequences for your company.
Many organizations operate under the mistaken belief that standard routines like deleting files or formatting a drive are sufficient for business-grade assets. This assumption is fundamentally flawed and dangerously common in commercial environments.
The Illusion of Deletion in a Business Context
Here's the hard truth: deleting a file on a hard drive doesn't actually erase the data. It just tells the operating system that the space where that file lived is now available to be overwritten. Until new data is physically saved in that exact spot on the drive's platter, the original file is still there, easily restorable with widely available data recovery software.
Formatting a drive seems more thorough, but it often works the same way. A "quick format" just wipes the address tables, leaving the underlying data completely untouched. Even a "full format" might not be enough to stop a determined thief using advanced forensic tools.
The real issue is that data is persistent by design. Hard drives are built to store information reliably, which, ironically, makes that information incredibly difficult to permanently remove without specialized, certified methods designed for commercial IT asset disposal.
The Real-World Risks of Lingering Corporate Data
The fallout from this lingering data getting into the wrong hands is severe and hits from all angles. A single improperly discarded hard drive from your business can set off a chain reaction of negative outcomes that can cripple your operations.
- Financial Penalties: Regulatory bodies across the United States don't mess around with data privacy violations. For example, Morgan Stanley was hit with a $35 million fine by the SEC for failing to properly decommission thousands of hard drives containing customer PII.
- Reputational Damage: A public data breach shatters customer trust, tarnishes your brand, and can lead to a mass exodus of clients. Rebuilding that trust is a long, expensive, and sometimes impossible, road for any U.S. business.
- Legal Liability: On top of regulatory fines, your company could face a mountain of costly lawsuits from customers, partners, or employees whose data was compromised because of simple negligence in your IT asset disposal process.
To keep data from sitting unsecured on active drives before they reach their end-of-life, technologies like BitLocker encryption are often used to protect information. But encryption doesn't solve the end-of-life disposal problem. The only way to guarantee that sensitive information on retired drives is gone for good is through professional, secure hard drive destruction provided by a certified commercial service provider like Beyond Surplus.
Choosing Your Data Destruction Method: A Guide for Businesses
Once you realize that just hitting 'delete' isn't enough for corporate assets, the next logical step is picking a certified method to destroy your hard drives for good. Not all methods are created equal. The right choice hinges on your security needs, any compliance regulations your business must follow, and whether the drive could be reused or resold. The three industry-standard methods are physical shredding, degaussing, and data sanitization.
It's critical for IT managers and business owners to make an informed decision. This visual breaks down why common practices like deleting or formatting files just don't cut it, leaving your business exposed.
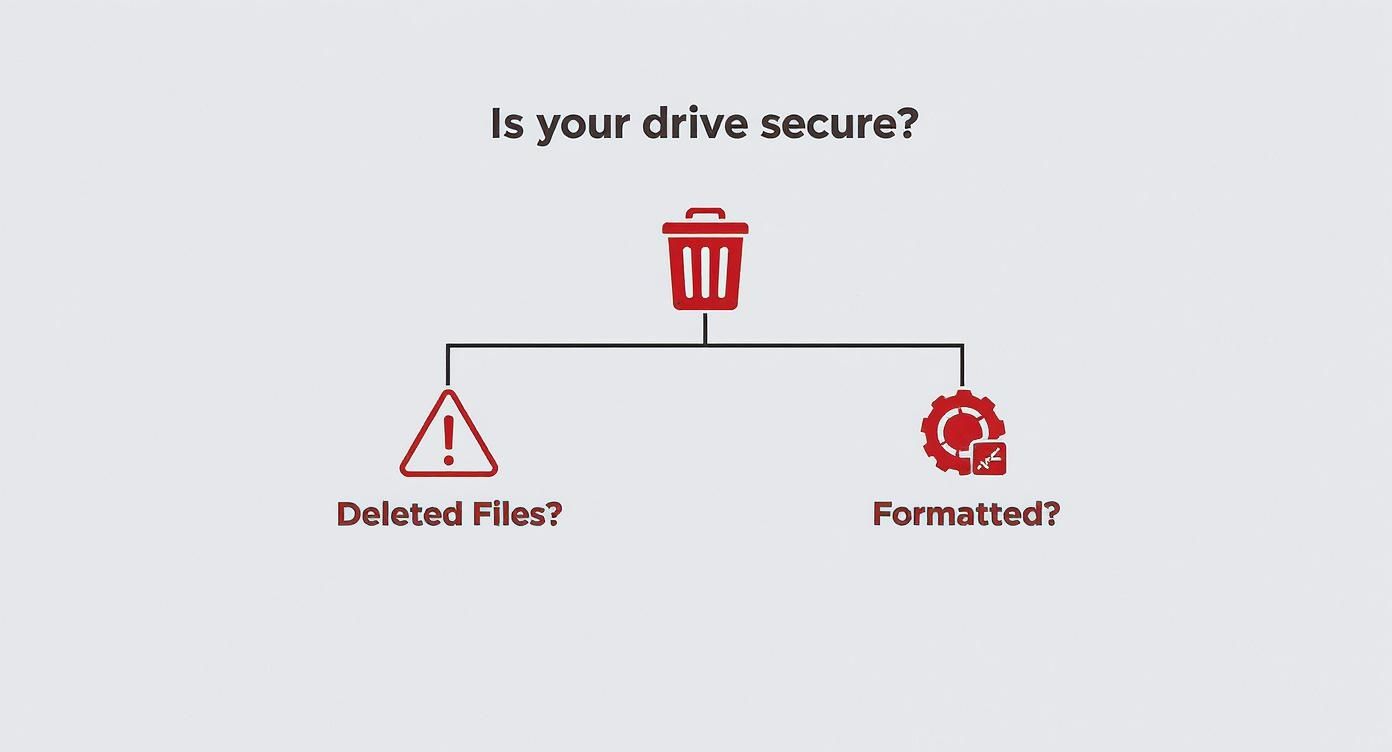
The key takeaway is simple: both deleting and formatting are reversible. Without certified destruction, that sensitive corporate data can still be recovered.
Physical Shredding: The Gold Standard for Business Disposal
Think of hard drive shredding like a high-security paper shredder, but built for steel and silicon. This method uses powerful, industrial-grade machines to physically pulverize drives into tiny, mangled pieces of metal. The process is absolute and completely irreversible, making it the most secure choice for business assets at the end of their life.
Because shredding obliterates the drive platters and internal parts where data lives, there is zero chance of recovery. This is why it’s the go-to method for devices holding sensitive intellectual property, customer PII, or classified information. To see exactly how this works, check out our comprehensive guide to secure hard drive shredding.
This definitive approach is a cornerstone of a rapidly growing industry. The global market for these services was valued around USD 1.5 billion in 2023 and is expected to climb to USD 3.6 billion by 2032, all thanks to increasing data security concerns for businesses across the United States.
Degaussing: A Magnetic Approach to Data Erasure
Degaussing is a less common but still effective method for traditional hard disk drives (HDDs) that store data magnetically. It involves blasting the drive with an incredibly powerful magnetic field, which completely scrambles and neutralizes the magnetic particles on the drive's platters. In short, it erases everything, making the drive useless and the data permanently gone.
However, degaussing comes with one massive catch for modern IT infrastructure:
Degaussing is completely ineffective on Solid-State Drives (SSDs). SSDs store data on flash memory chips (NAND), which aren't magnetic. Using a degausser on an SSD does absolutely nothing to the information, creating a dangerous false sense of security for your business.
For this reason, degaussing is mostly used for older magnetic media like HDDs and backup tapes. As SSDs have become the norm in corporate environments, physical shredding has largely taken over as the universal solution.
Data Sanitization: Overwriting for Secure Reuse and Value Recovery
Unlike shredding and degaussing, data sanitization (or secure wiping) is a software-based method. It’s designed to erase data completely while leaving the hard drive intact and ready for reuse. This process uses specialized software to write over every single sector of the drive with random binary data—a stream of ones and zeros.
This overwriting can be done multiple times (called "passes") to meet specific compliance standards, like those from the Department of Defense (DoD 5220.22-M) or NIST 800-88.
- Best Use Case: Data sanitization is perfect for businesses that want to get some value back from their used IT assets, either by reselling them or using them again internally.
- Verification: After the process is done, the software generates a certified report to prove the wipe was successful and all data is unrecoverable.
- Limitation: This method only works on functional hard drives. If a drive is damaged or won't turn on, the software can't access it to perform the overwrite. For failed drives, physical destruction is the only safe bet.
Comparison of Hard Drive Destruction Methods for Business
Choosing the right data destruction method can feel complicated, but breaking it down by key factors makes the decision much clearer for business leaders. The best approach depends on whether you need to reuse the asset, what compliance standards you have to meet, and how sensitive the data is.
Here's a side-by-side look at the three primary methods to help your U.S. business decide.
| Method | How It Works | Best For | Asset Reusability | Compliance Level |
|---|---|---|---|---|
| Physical Shredding | Industrial machinery grinds drives into small, irrecoverable metal fragments. | End-of-life assets, failed drives, or devices with highly sensitive data. | None. The drive is completely destroyed. | Highest. Meets all major U.S. standards (HIPAA, FTC, NIST). |
| Degaussing | A powerful magnetic field scrambles the magnetic domains on HDD platters, erasing all data. | Older magnetic media like HDDs and backup tapes. Not effective on SSDs. | None. The drive is rendered inoperable. | High (for magnetic media only). |
| Data Sanitization | Specialized software overwrites every sector of the drive with random data, making original data unrecoverable. | Functional drives with resale or reuse value. | Yes. The drive remains fully functional. | High. Certified to meet standards like NIST 800-88 and DoD 5220.22-M. |
Ultimately, your choice comes down to balancing security with value recovery. For drives being permanently retired, shredding offers absolute peace of mind. For functional drives with resale potential, certified sanitization provides a secure and financially smart alternative.
Meeting Critical U.S. Compliance Standards
When it comes to your company's old hard drives, secure destruction isn't just a good idea—it's the law. For any modern U.S. business, failing to comply with data privacy regulations can open the door to crippling fines, messy legal battles, and the kind of reputational damage that’s hard to come back from.
This isn't about suggestions; it's about strict requirements. A casual approach to tossing old corporate IT gear isn’t just sloppy—it’s a direct violation that puts your entire organization at risk. That's why thinking of professional IT asset disposition (ITAD) as a cost is a mistake. It’s one of the most important risk management strategies your business can have.
Navigating Key U.S. Data Privacy Regulations
Several major regulations dictate exactly how businesses in the United States must handle and destroy sensitive data. They all come from different angles, but the core message is the same: you are responsible for protecting data from the moment it’s created to the moment it’s permanently destroyed.
- HIPAA (Health Insurance Portability and Accountability Act): This is the big one for any U.S. organization touching Protected Health Information (PHI). The HIPAA Security Rule is crystal clear: you must have policies for the final disposal of electronic PHI and the hardware it lives on.
- FACTA (Fair and Accurate Credit Transactions Act): Created to fight identity theft, this federal law’s Disposal Rule requires any business with consumer credit information to take reasonable steps to destroy it for good. That means physically shredding hard drives from old office PCs, not just deleting files.
- GDPR (General Data Protection Regulation): If your U.S. business serves anyone in the European Union, GDPR’s standards are incredibly high. It enshrines the "right to be forgotten," meaning you need a bulletproof, verifiable process to permanently erase personal data when requested.
These rules all point to one thing: your business needs a formal, documented process. When an auditor comes knocking, you have to be able to prove you did everything right to make that data unrecoverable.
The NIST 800-88 Guidelines Explained for Businesses
So, what does "doing it right" actually look like? The National Institute of Standards and Technology (NIST) gives us the playbook with its Special Publication 800-88. This isn't just another government document; it's the gold standard for media sanitization, referenced by federal agencies and top security experts across the United States.
Instead of vague advice, NIST provides a clear, tiered framework for making data disappear forever.
- Clear: This involves using software-based overwriting techniques to sanitize data. It's effective for lower-risk information and has the big advantage of allowing the drive to be reused.
- Purge: This method goes deeper, using techniques like degaussing or cryptographic erasure that make data recovery impossible even with advanced forensic lab equipment.
- Destroy: This is the final answer. It’s the physical obliteration of the storage media, rendering it completely unusable through shredding, melting, or pulverizing. For the most sensitive corporate data or for drives at the true end of their life, this is the only way to be 100% certain.
Getting familiar with these tiers is the key to making smart, cost-effective decisions about your old hardware. To get a much deeper dive into these protocols, check out our complete overview of the NIST SP 800-88 guidelines and see how they apply directly to your corporate assets.
The Power of a Certificate of Destruction for Your Business
Let's say your U.S. business is in an audit. How do you prove you followed all these rules? The answer is your Certificate of Destruction (CoD). This document is much more than a receipt. It’s your official, legally defensible record that formally transfers liability from your shoulders to your ITAD partner’s.
A Certificate of Destruction is your primary evidence of due diligence. It formally documents the secure and permanent disposal of your data-bearing assets, protecting your business from claims of negligence.
A legitimate CoD isn't just a piece of paper. It has to include specific details to be valid:
- A unique serial number for tracking the job.
- Transfer of custody information, including the exact date and location of pickup.
- An itemized list of the destroyed media, down to the individual serial numbers.
- The specific method of destruction used (e.g., shredding to a certain particle size).
- A clear statement that the process complied with standards like NIST 800-88.
Without this certificate, you have no verifiable proof of compliance. This ties directly into broader security frameworks; for example, understanding something like the ISO 27001 certification shows how audited controls and documented proof are central to modern information security. Your CoD is a critical piece of that puzzle.
On-Site Versus Off-Site Destruction for U.S. Companies
So, where should your corporate hard drives meet their end? It's a bigger decision than you might think, and it directly impacts your security, logistics, and budget. You've got two main paths: bring the destruction to your front door (on-site) or securely ship your assets to a specialized facility (off-site). Both get the job done, but they cater to very different business needs.
This choice isn't just about convenience. It’s a fundamental decision about how your business manages risk and how much transparency you need. Getting to know the ins and outs of each model is the only way to align your disposal strategy with your company's unique security and compliance demands.
The Case for On-Site Destruction for Maximum Business Security
On-site destruction is as straightforward as it sounds. A mobile shredding truck, packed with industrial-grade equipment, rolls right up to your office, data center, or facility anywhere in the United States. The beauty of this method is the absolute transparency—you can stand there and watch the entire process from beginning to end.
Its biggest selling point is a completely unbroken chain of custody. Your hard drives never leave your sight until they’re reduced to a pile of tiny, useless fragments. This wipes out any risk tied to transport or third-party handling, which is precisely why it’s the gold standard for organizations with ironclad security policies.
- Maximum Security: Watching the shredder do its work gives you undeniable proof and total peace of mind.
- Immediate Verification: You can confirm with your own eyes that every single drive has been destroyed as promised.
- Compliance Certainty: For U.S. industries governed by HIPAA or FACTA, on-site destruction provides the most direct, defensible proof of due diligence.
This approach is perfect for businesses dealing with sensitive intellectual property, classified government data, or large volumes of customer PII. To get a better sense of the process, check out our deep dive on on-site shredding services.
The Advantages of Off-Site Destruction for Businesses
Off-site destruction is the flip side of the coin. A certified ITAD partner like Beyond Surplus shows up at your U.S. location, collects your assets, secures them in locked containers, and hauls them away in a GPS-tracked vehicle to their secure facility. While you aren't physically present for the destruction, the whole process is wrapped in tight security protocols—think secure loading docks, 24/7 surveillance, and strict access controls.

Often, this is the more efficient and budget-friendly option, especially for companies retiring a massive number of assets or those that simply don't have the space for a large shredding truck.
The key to secure off-site destruction is a meticulously documented and verifiable chain of custody. A reputable partner will provide detailed reports, including serialized asset tracking from the moment of pickup to the final Certificate of Destruction.
This model works great for large-scale IT refresh projects, data center decommissioning, or any routine retirement where logistics and efficiency are top priorities for your business.
Making the Right Choice for Your U.S. Business
The best approach always comes down to a careful balance of your organization's risk tolerance, budget, and operational realities.
| Factor | On-Site Destruction | Off-Site Destruction |
|---|---|---|
| Security | Highest level; assets never leave the premises intact. | High level; relies on a secure chain of custody and facility protocols. |
| Transparency | Complete; you can witness the entire process. | Documented; relies on reporting, video logs, and audits. |
| Cost | Generally higher due to mobilization and dedicated equipment. | Often more cost-effective, especially for larger volumes. |
| Logistics | Requires space for a large truck and coordination for scheduling. | Simpler pickup process managed entirely by the vendor. |
Hard drive shredding, whether done on-site or off-site, is a huge part of the data security market for a reason. The global market for these services was valued at around USD 0.72 billion in 2024 and is expected to climb to USD 1.2 billion by 2033. That growth underscores just how vital this service is for corporate risk management. You can discover more insights about the hard drive shredding services market growth and what's driving it.
Ultimately, when performed by a certified and trusted vendor, both methods deliver compliant and totally secure hard drive destruction for your U.S. business.
How to Select a Certified ITAD Partner in the U.S.
Your company’s data security is only as strong as the vendor you trust to handle it. Choosing an IT Asset Disposition (ITAD) partner is a huge decision, one that goes way beyond just picking the lowest quote. A real security partner will give your U.S. business a transparent, compliant, and legally solid process for secure hard drive destruction, protecting you from the nightmare of a data breach.
The whole point is to look past the sales pitch and find a partner who delivers total peace of mind. A slick brochure doesn't mean anything if the vendor is cutting corners on their chain of custody or compliance.

Non-Negotiable Industry Certifications for U.S. Businesses
Certifications are your fastest filter for vetting a potential ITAD partner. They aren't just fancy logos for a website; they prove a vendor has committed to tough, third-party audits covering security, environmental rules, and professional operations. In the U.S. ITAD world, two certifications are absolute must-haves.
- R2v3 (Responsible Recycling): Think of the R2v3 standard as a complete rulebook for data security, environmental safety, and worker health. An R2v3-certified company has proven they follow strict procedures for wiping and destroying data, so you know your sensitive corporate information is handled correctly.
- e-Stewards: This certification is famous for its incredibly strict environmental standards, especially its ban on shipping hazardous e-waste to developing nations. It also has tough data security requirements, making it another top-tier credential for any U.S. business that cares about compliance and corporate social responsibility.
If a vendor you're considering doesn't have these core certifications, that’s a major red flag. They are the baseline for proving a commitment to professional and ethical IT asset management.
Vetting Your Vendor: A Checklist for U.S. Businesses
Once you have a shortlist of certified vendors, it’s time to dig in. The answers to these questions will tell you everything you need to know about their operation. Use this checklist when you talk to them.
- Chain of Custody: "Walk me through your chain-of-custody process, from the second my assets leave our U.S. office to their final destruction. What paperwork do I get at each step?"
- Facility Security: "What kind of security do you have at your processing facility? I'm talking about 24/7 monitored surveillance, controlled access, and locked-down storage for drives."
- Employee Screening: "Do all employees who handle our equipment go through serious background checks and regular security training?"
- Insurance and Liability: "What does your liability insurance cover? Does it specifically mention data breaches? Can I see a certificate of insurance?"
- Downstream Vendor Management: "How do you check on your downstream recycling partners? Can you show me proof of their certifications?"
- Reporting and Documentation: "What kind of report will I get at the end? Will it be a serialized Certificate of Destruction that will stand up in a U.S. audit?"
A partner who is confident in their process will have no problem giving you clear, detailed answers to every single one of these questions.
Understanding the Financial and Security Stakes for U.S. Companies
The growing demand for professional destruction equipment really drives home how critical this process is. The market for hard drive destruction equipment was valued at around USD 2.69 billion in 2024 and is expected to jump to USD 4.23 billion by 2032. This isn't just about buying shredders; it reflects how urgently U.S. businesses need to shield themselves from data breaches and the massive liability that comes with improper disposal.
Your ITAD vendor isn't just a service provider—they're an extension of your security and compliance team. Their process has to be strong enough to hold up in court and protect your company's good name.
Ultimately, picking the right partner is all about managing risk. By focusing on certified vendors and asking the tough questions, you can be sure your company's end-of-life asset strategy is secure, compliant, and defensible. To get a better feel for the full range of services a qualified partner should offer, check out our guide on what is IT asset disposition. It’ll give you the knowledge you need to make the best possible choice.
Common Questions About Hard Drive Destruction for Businesses
When it comes to getting rid of old IT assets, many business owners and IT managers across the United States have the same nagging questions. Bad advice can lead to huge security gaps, so getting straight, honest answers is the only way to protect your company. Let's clear up some of the most common myths and questions about secure hard drive destruction for commercial clients.
Is Deleting Files and Formatting a Hard Drive Enough to Secure Our Business Data?
Absolutely not. This is probably the single most dangerous myth in corporate data security today. When you delete a file or run a standard format, you're not actually erasing anything. All you're doing is removing the signposts that tell the operating system where to find the data.
The actual data remains on the drive's platters, and it's shockingly easy to get back with software anyone can download. Real security for your business means using professional methods—like physical shredding, degaussing, or NIST-compliant wiping—that make the data gone for good.
What Is a Certificate of Destruction and Why Is It Important for My Business?
A Certificate of Destruction (CoD) is much more than a simple receipt. It's a formal, legally binding document that acts as your official audit trail, proving your business disposed of its data-bearing devices correctly and in line with U.S. regulations like HIPAA, FACTA, and the FTC Disposal Rule. It's your number one defense if an auditor or regulator ever comes knocking.
Simply put, a proper CoD formally transfers the liability for the destroyed assets from your company to your certified ITAD vendor. Without it, you have no proof of due diligence, opening your business up to massive fines and legal trouble.
To be valid, a CoD needs to include very specific details:
- A unique serial number for that specific job.
- A detailed list of every asset destroyed, including their individual serial numbers.
- The exact date and location where the destruction took place.
- The method used (e.g., "shredded to 2mm particle size").
- A statement confirming compliance with standards like NIST SP 800-88.
How Do You Securely Destroy Solid-State Drives (SSDs) for a Business?
This is a fantastic question because SSDs and traditional hard disk drives (HDDs) are completely different animals. An SSD stores data on tiny flash memory chips, not on magnetic platters. This means that methods designed for magnetic media, like degaussing, are totally useless on an SSD.
The only foolproof method for the secure hard drive destruction of an SSD is to physically demolish it. The drive must be shredded into particles so small that the internal NAND flash memory chips are completely pulverized. You have to make sure your ITAD partner uses industrial shredders specifically designed for SSDs, which grind down to a much finer particle size needed to destroy those tiny, data-packed components.
What Is the Difference Between NIST Purge and Destroy for Corporate Assets?
These terms come straight from the gold standard in U.S. data security, the NIST SP 800-88 Guidelines for Media Sanitization. They define two very different levels of data destruction, and knowing the difference helps your business match the right method to your security needs and the asset's future.
NIST Purge: This is a software-based or cryptographic method that makes data recovery practically impossible, even with state-of-the-art lab equipment. The big advantage? The hard drive itself isn't damaged, so it can be safely reused or resold, which is great for recovering value from your old corporate equipment.
NIST Destroy: This is the end of the line. It makes data recovery physically impossible because the media itself is ruined. We're talking about shredding, melting, or pulverizing the drive into tiny pieces. The drive is completely unusable afterward. For drives that held your company's most sensitive data, are old, or have failed, this is the only way to get 100% peace of mind.
Picking the right method and the right partner for your IT asset disposal is one of the most important security decisions your U.S. business will make. For certified, compliant services that fit your organization's needs, contact Beyond Surplus. We provide nationwide pickup for businesses across the United States, guaranteeing your corporate data is destroyed securely and responsibly. Schedule your secure electronics recycling pickup with Beyond Surplus today.



