For any business in Georgia, compliant IT disposal isn’t just about making space in the storage closet; it's a fundamental part of your security and legal framework. When your enterprise properly disposes of old computers, servers, and phones, you're ensuring that sensitive company and customer data is permanently destroyed. This single step protects your organization from the nightmare of a data breach and the heavy fines that follow.
Why Secure IT Disposal Is Non-Negotiable for Georgia Enterprises

Those piles of old office computers and retired servers are much more than just clutter—they're a ticking time bomb of business risk. Every single device, whether it's a sales team laptop or a decommissioned server from your data center, is a treasure trove of sensitive information. Disposing of this hardware the wrong way is like leaving unlocked filing cabinets full of your most confidential files out on the curb.
Think about what's actually stored on these retired assets:
- Customer financial records and personally identifiable information (PII)
- Employee data, including social security numbers and payroll details
- Your company's proprietary trade secrets and intellectual property
- Confidential patient health information (PHI)
Failing to sanitize this equipment before it leaves your sight opens your business up to massive liability. All it takes is one misplaced hard drive to trigger a data breach, kicking off a chain reaction of costly notification requirements, regulatory investigations, and permanent damage to your brand's reputation.
The High Stakes of Non-Compliance
For businesses operating in Georgia, a handful of federal laws create a strict rulebook for data security that covers a device's entire lifecycle, right down to its final disposal. These aren't just suggestions; they are enforceable regulations with painful penalties for getting it wrong.
The key concept here is "cradle-to-grave" liability. As the one who created or collected the data, your organization is legally on the hook for protecting it until it's verifiably destroyed. That responsibility doesn't go away just because you handed the equipment to a disposal vendor.
To give you a clearer picture, here’s a quick rundown of the major regulations and what’s at risk for Georgia businesses.
Key Compliance Risks for IT Disposal in Georgia
| Regulation | Who Is Affected | Core Disposal Mandate | Consequences of Failure |
|---|---|---|---|
| FTC Disposal Rule | Virtually all businesses handling consumer information. | Must take "reasonable measures" to destroy consumer data to prevent unauthorized access. | FTC enforcement actions, fines, and potential civil litigation. |
| HIPAA | Healthcare providers, health plans, and their business associates. | Must implement secure procedures for the final disposal of electronic protected health information (ePHI). | Severe civil and criminal penalties, with fines up to $1.5 million per violation category per year. |
| GLBA | Financial institutions (banks, lenders, investment firms, etc.). | Required to protect consumers' private financial data, including during the disposal of records and hardware. | Fines up to $100,000 for each violation, plus potential imprisonment for individuals. |
These regulations make it clear that simply hoping for the best is not a viable strategy. A structured, documented disposal process is the only way to ensure you're covered.
Shifting from a Task to a Strategy
Ultimately, you have to treat compliant IT disposal in Georgia as a core piece of your cybersecurity strategy. This isn't a simple cleanup job for the facilities team; it’s a critical risk management function that IT and leadership must oversee.
Partnering with a certified IT Asset Disposition (ITAD) expert ensures every device is handled securely, all data is destroyed according to NIST standards, and you get the paperwork you need to prove it. Learning how a formal approach to Georgia electronics recycling shields you from these risks is the first step. This proactive stance turns a huge potential liability into a secure, closed loop in your asset management lifecycle, protecting your bottom line and the trust you’ve worked so hard to build.
Making Sense of Georgia's Data Disposal Rules
When it comes to getting rid of old IT gear in Georgia, knowing the legal landscape is the first step to protecting your business. The rules for data destruction aren't just suggestions—they’re firm requirements with serious penalties if you ignore them. While Georgia doesn't have a single, massive e-waste law for businesses, a powerful mix of federal laws and industry standards creates a clear standard you’re expected to meet.
For any business here in Georgia, this legal framework really rests on three main pillars of federal law, each focused on a different kind of sensitive information.
The Federal Laws Driving Compliance
These laws apply to your business no matter where you are in the state, from a high-rise in Atlanta to a warehouse in Savannah. They set the baseline for what counts as a "reasonable measure" to protect data when you’re getting rid of old hardware.
- The FTC Disposal Rule: This one has the widest reach. It applies to any business that handles consumer information, from credit reports to background checks. The rule is simple: you must take appropriate steps to destroy that data before you toss out any device or record.
- HIPAA (Health Insurance Portability and Accountability Act): If you're in the healthcare world—a hospital, insurance provider, or even one of their business partners—HIPAA is the law of the land. It demands strict, documented protocols for the secure and permanent destruction of all electronic protected health information (ePHI).
- GLBA (Gramm-Leach-Bliley Act): This one’s for financial institutions like banks, investment firms, and mortgage lenders. GLBA has specific rules requiring the secure disposal of nonpublic personal information (NPI) to protect consumer financial privacy.
Dropping the ball on these federal rules can lead to some painful consequences, including huge fines and a damaged reputation. This is exactly why having a formal IT asset disposal process isn't just a good idea; it's essential.
Georgia's De Facto Standard of Care
Even though Georgia's own laws are pretty quiet on commercial e-waste, they still hold businesses 100% liable for any data breach that comes from sloppy end-of-life data destruction. If data gets out from an old hard drive, SSD, or server you thought was taken care of, you’re on the hook for mandatory breach notifications and legal enforcement.
The challenge is only getting bigger. The U.S. electronics recycling market is projected to hit an incredible $27.7 billion by 2025 as more and more companies try to get a handle on these security and environmental duties.
This is where professional certifications come in to fill the legislative gap. They create a de facto standard that regulators and courts look to as a benchmark for best practices.
Think of it this way: The law tells you that you must protect the data, but certifications like R2v3 show you how. They provide a real, auditable framework for doing it right.
An R2v3 (Responsible Recycling) certification is a global standard that proves an ITAD vendor meets the highest levels of data security, environmental protection, and worker safety. When you work with an R2v3-certified provider for compliant IT disposal in Georgia, you’re actively demonstrating your due diligence.
This certification basically serves as your proof that you took all the reasonable and necessary steps to protect sensitive information, which goes a long way in reducing your liability. You can learn more about how to structure your own process by checking out our complete guide on secure IT asset disposal in Georgia. By understanding both the federal mandates and the industry standards that define compliance, you can build a disposal program that truly protects your organization.
Choosing Your Data Destruction Method
Once you know the rules you have to follow, the next logical step is figuring out the best way to permanently erase your data. For any Georgia business, this decision is a critical control point in the entire compliant IT disposal process. It’s definitely not a one-size-fits-all choice; the right approach really hinges on how sensitive your data is, the kind of IT assets you have, and your organization's comfort level with risk.
Making the right choice is a bit like deciding between shredding a top-secret document into fine confetti versus just blacking out lines with a marker. Both try to hide the information, but one offers an irreversible guarantee it's gone for good.
Software-Based Wiping versus Physical Destruction
At a high level, you have two main options: software-based data wiping (also called sanitization) and good old-fashioned physical destruction. Each one has its place and aligns with different business needs, especially when you're thinking about getting some money back from your old equipment.
Software-Based Wiping (Data Sanitization)
This method uses highly specialized software to overwrite every single bit of data on a hard drive or SSD with random characters. It usually does this in multiple passes to be thorough. The gold standard for this process is NIST 800-88, a set of guidelines that has become the industry benchmark for media sanitization.
- Primary Advantage: The biggest win here is that the storage device remains perfectly intact and functional. This means the asset—like a laptop, server, or workstation—can be refurbished and resold, turning a disposal cost into a potential revenue stream.
- Best Use Case: This is the ideal route for newer, still-valuable equipment where you want to recoup some of your initial investment. It’s a completely secure and compliant method for most types of business data.
Physical Destruction (Shredding)
This is as final as it gets. Physical destruction involves feeding hard drives, SSDs, backup tapes, and other storage media into an industrial shredder that grinds them down into small, mangled fragments. There’s no coming back from that.
- Primary Advantage: It gives you absolute, visual proof that the data is gone forever. There is zero chance of recovery because the physical device no longer exists in a usable form.
- Best Use Case: This is a must for devices containing top-secret intellectual property, highly sensitive government data, or for older, broken assets that have no resale value anyway.
The flowchart below gives you a clear visual of the decision-making process based on the type of data your organization handles. It’s a great first step for planning compliant IT disposal here in Georgia.
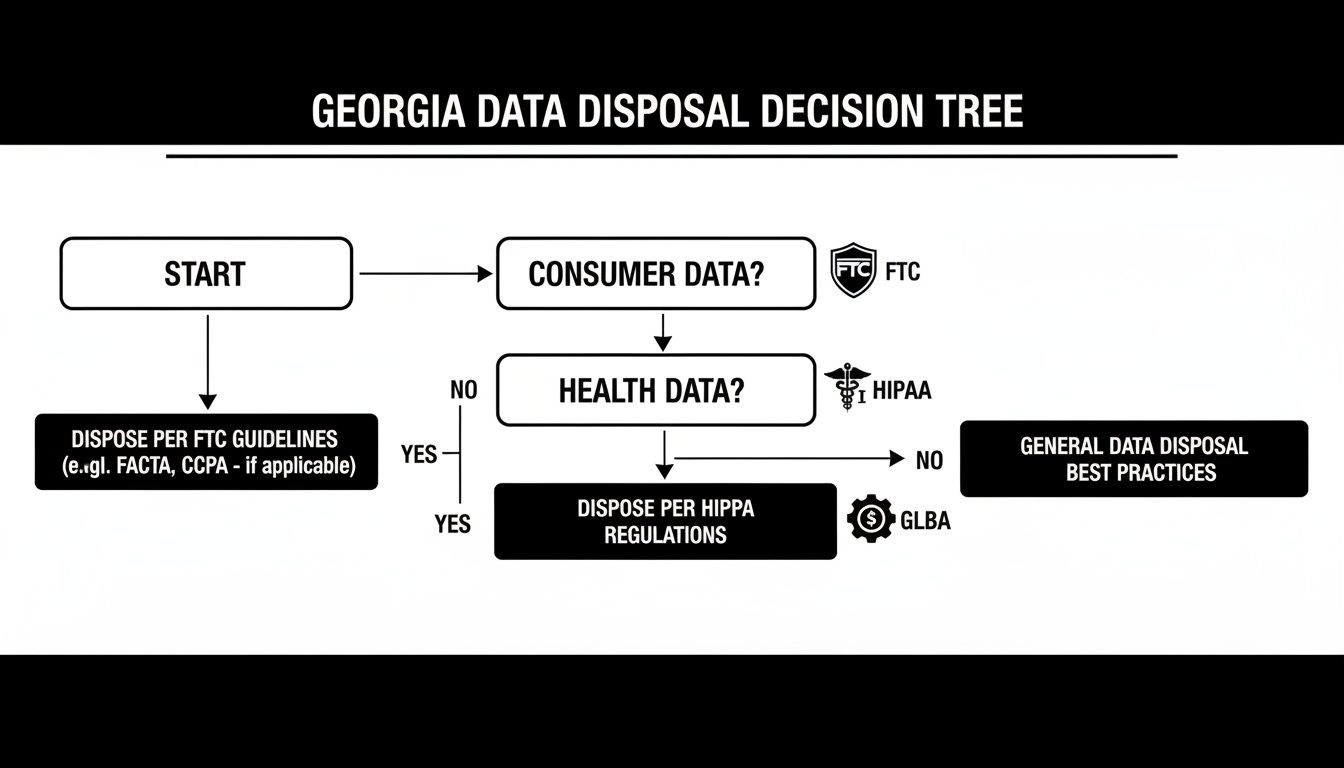
As you can see, federal regulations like the FTC Disposal Rule, HIPAA, and GLBA directly shape your disposal strategy depending on the kind of information you’re protecting.
On-Site vs. Off-Site Destruction: A Key Logistical Choice
After you've decided how to destroy the data, you need to decide where it will happen. This choice has a direct impact on your chain of custody and overall security protocols.
On-Site Data Destruction
With on-site services, a mobile shredding truck or data wiping station comes directly to your facility in Georgia. Your team can literally stand there and watch the physical destruction or sanitization of hard drives before the equipment ever leaves your property.
On-site destruction offers the tightest possible chain of custody. Because the assets never leave your control while still holding data, the risk of something going wrong in transit is completely eliminated. This provides maximum peace of mind, especially for high-security environments.
Off-Site Data Destruction
In this model, your IT assets are securely packed and transported in a locked, GPS-tracked vehicle by a certified ITAD partner to their secure facility for destruction. The whole process is documented, tracked by serial number, and you receive certified proof of destruction upon completion.
For Georgia businesses looking to weigh their options, you can explore a variety of certified security and data destruction services that help balance cost, convenience, and risk.
While both methods are secure when you work with a certified vendor, the decision often comes down to your internal security policies and budget. On-site services offer unmatched security and transparency, but off-site services are often more cost-effective and efficient for larger volumes of assets. A good partner will help you walk through your specific needs to land on the most appropriate and compliant solution.
Comparing Data Destruction Techniques for Business Assets
To make the decision clearer, it helps to see the methods laid out side-by-side. Each technique has its ideal application, compliance standing, and unique considerations that can influence which is right for a particular piece of equipment.
| Method | Ideal For | NIST Compliance | Primary Advantage | Key Consideration |
|---|---|---|---|---|
| Software Wiping (NIST 800-88) | Laptops, Servers, PCs, loose HDDs/SSDs with resale value. | Meets or exceeds NIST 800-88 Purge/Clear standards. | Preserves the hardware for reuse and remarketing, maximizing value recovery. | Requires functional hardware; process time varies by drive size and type. |
| Physical Shredding | End-of-life hard drives, damaged media, backup tapes, highly sensitive data. | Meets NIST 800-88 Destroy standard. | Provides absolute, visually verifiable proof of destruction. Irreversible. | Destroys the asset, eliminating any potential for resale or reuse. |
| Degaussing | Magnetic media like HDDs and certain data tapes. | Meets NIST 800-88 Purge standard for magnetic media. | Extremely fast and effective for large batches of magnetic drives. | Ineffective on SSDs and flash media; renders HDDs inoperable. |
| Cryptographic Erasure | Self-Encrypting Drives (SEDs) and modern SSDs. | Meets NIST 800-88 Clear standard when properly implemented. | Nearly instantaneous data sanitization by deleting the encryption key. | Relies on the drive's built-in encryption; verification is critical. |
Ultimately, choosing the right method is about aligning your organization's security posture with your asset recovery goals. A trusted ITAD partner can provide a blended approach, using software wiping for valuable assets and physical shredding for everything else, ensuring every device is handled appropriately.
How Documentation Transfers Your Liability
Let's be clear: the job of compliant IT disposal in Georgia isn't finished when the truck pulls away from your facility. In fact, one of the most critical steps happens after your assets are gone—getting the right documentation in your hands. This paper trail is the single most important element in shutting down your risk and proving you did everything by the book.
Many businesses make the mistake of treating a Certificate of Data Destruction like just another receipt. That's a dangerous way to think. This document is your legal proof that you fulfilled your data security obligations. It’s the final, essential step that shields your organization from liability.
More Than a Receipt—It's a Legal Shield
Think of a Certificate of Data Destruction like the deed to a house. When you sell your home, the signed deed legally transfers ownership and all the responsibilities that come with it to the new owner. It’s the same principle here. A properly executed certificate formally transfers the liability for the data on your retired assets from your company to your ITAD partner.
Without this document, you're stuck in a legal gray area. If one of your old hard drives were to turn up years later and cause a data breach, the burden would be on you to prove you took responsible steps. The certificate closes that loop for good, giving you clear, undeniable evidence for any audit or legal challenge.
Anatomy of an Effective Certificate
A generic, one-page document won’t cut it. To be a credible defense, your documentation has to be detailed and transparent. It needs to create an unbroken chain of custody from your door right up to the point of final disposition.
A compliant certificate must contain specific, auditable information:
- Unique Serial Numbers: Every single data-bearing device (hard drive, SSD, server) has to be individually listed by its serial number. This creates a one-to-one link between the asset that left your facility and the one that was destroyed.
- Method of Destruction: The document must clearly state how each asset was handled—whether it was physical shredding or data sanitization compliant with NIST 800-88 standards.
- Date and Location of Destruction: This confirms exactly when and where the sanitization or destruction took place, adding another layer of verification.
- Statement of Liability Transfer: The certificate should include explicit language stating that the ITAD vendor accepts all liability for the data on the listed assets from that point forward.
This level of detail is non-negotiable. It transforms the document from a simple acknowledgment into a robust legal instrument. It proves you didn’t just hand off your equipment; you managed its end-of-life with precision and care, fulfilling your obligations under regulations like the FTC Disposal Rule and HIPAA.
You can learn more about the specifics of what makes a hard drive destruction certificate a legally sound document that protects your business. Ultimately, viewing documentation not as a formality but as your ultimate liability shield is a cornerstone of any successful and compliant IT disposal program.
Turning Old Tech Into New Revenue

What if your compliant IT disposal Georgia process could pay for itself—or even turn a profit? For too long, businesses have treated retired technology as just another liability. It sits in a closet, racking up storage fees and compliance risks until it's time to pay someone to destroy it.
It's time for a different perspective. Let's stop seeing old tech as a burden and start seeing it for what it truly is: a hidden asset waiting to be unlocked.
This strategic shift is made possible by something called IT Asset Value Recovery (ITAVR). It's a formal process for turning outdated equipment into a real revenue stream. Instead of shredding every single device, ITAVR pinpoints the assets that still have life left in them and value in the secondary market. Laptops, servers, networking gear—you'd be surprised what can be securely refurbished and sold, directly offsetting the costs of your entire disposal program.
Tapping Into the Thriving Refurbished Market
The demand for high-quality, refurbished electronics is absolutely booming, and that creates a massive financial opportunity for Georgia businesses. When you work with a certified IT Asset Disposition (ITAD) partner, they handle the entire value recovery process for you.
Here’s how it typically works, seamlessly and securely:
- Secure Logistics: Your equipment is picked up and transported to a secure facility under a strict, documented chain of custody.
- Data Sanitization: Every device with a hard drive or storage undergoes a certified data wipe, usually meeting NIST 800-88 standards. This ensures compliance while keeping the hardware intact.
- Testing and Grading: Each asset is then professionally tested, graded for its cosmetic condition, and prepped for resale.
- Remarketing: Your ITAD partner uses their established sales channels to find buyers and get the best possible price for the refurbished gear.
- Revenue Sharing: A portion of the sales proceeds comes right back to your organization, either as a credit against your disposal fees or as a direct check.
This approach flips the script entirely, turning a compliance-driven expense into a smart financial move that boosts your bottom line.
From Cost Center to Strategic Advantage
This isn't just a niche idea; it's fundamentally changing how Georgia businesses approach IT compliance. The refurbished electronics market is projected to hit $32.7 billion in 2025 and is on track to explode to $84.9 billion by 2034.
North America's ITAD industry is valued at $4.85 billion in 2025 and is climbing toward $6.59 billion by 2030, with strategic disposition being the key to recovering that leftover value. For small and medium-sized businesses, which make up a massive 63.90% of the market, this shift from cost to credit is a total game-changer. You can find more insights on the growth of the refurbished electronics market to see just how big this opportunity is.
By integrating value recovery into your disposal program, you essentially create a self-funding mechanism for security and compliance. The cash generated from reselling valuable assets can easily cover the cost of destroying non-valuable or highly sensitive equipment, making best-practice security financially sustainable.
On top of the financial benefits, embracing ITAVR is a huge win for your corporate sustainability goals. Extending the life of electronics through refurbishment is a core principle of the circular economy. It cuts down on e-waste, conserves the resources needed to build new products, and polishes your company's environmental credentials.
Finding a partner who can manage both secure destruction and value recovery gives you a complete, compliant, and financially intelligent solution for your end-of-life IT.
Your Georgia ITAD Partner Vetting Checklist
Choosing the right IT Asset Disposition (ITAD) partner is probably the most critical decision you'll make when it comes to compliant IT disposal in Georgia. This isn’t like picking any old logistics vendor; you're handing over your data security, your legal compliance, and even your brand's reputation.
The right partner is your shield. The wrong one can expose you to some serious risk. This checklist will walk you through the essential questions you need to ask to find a provider who can genuinely protect your organization.
Verifying Core Certifications and Insurance
Before you even get to services or pricing, start with the non-negotiables. Think of these credentials as the foundation of a trustworthy partnership—they prove the vendor operates at the highest industry standards.
- Are you R2v3 or e-Stewards certified? These are the gold standards for responsible electronics recycling and data security. A vendor with either certification has been through tough third-party audits, confirming their processes are secure, environmentally sound, and safe. You can learn more about why this matters in our guide explaining what R2 certification is.
- Can you provide proof of insurance? Ask to see their Certificates of Insurance. A legitimate ITAD provider must carry specific policies, including Data Breach/Cyber Liability and Pollution Liability insurance, to cover any potential screw-ups during transit or processing.
Evaluating Data Destruction Capabilities
Next, you need to dig into their data destruction methods. This is the heart of compliant disposal, and you need absolute certainty that their process is rock-solid.
The goal here is simple: confirm they can provide an auditable, legally defensible process. If you get vague answers or see a lack of detailed documentation, those are huge red flags. Honestly, it should disqualify them on the spot.
Here are the key questions to ask:
- What data destruction standards do you follow? The only answer you want to hear is NIST 800-88.
- Do you offer both on-site and off-site destruction services? Flexibility is a good sign of a capable partner.
- Can you provide serialized reporting? This is non-negotiable for creating a defensible audit trail.
- What's your process for verifying a successful data wipe?
Assessing Logistics and Chain of Custody
Finally, get a clear picture of how they handle your assets from the moment they leave your building. A secure chain of custody is everything—it prevents data from walking out the door during transport.
The North American ITAD market is projected to hit $4.85 billion in 2025 and grow to $6.59 billion by 2030, with small and medium businesses making up a massive 63.90% of that demand. For Georgia businesses in hubs like Atlanta and Smyrna, a partner who has mastered secure logistics is critical to avoiding the harsh penalties under the FTC Disposal Rule, HIPAA, and GLBA.
Make sure you ask potential partners:
- What security measures do you use during transport? Think locked trucks and GPS tracking.
- Are your logistics staff background-checked and trained in data security?
- How are my assets tracked from pickup all the way to final disposition?
Running through this checklist ensures you pick a partner for compliant IT disposal Georgia who does more than just haul away old equipment—they take on your risk so you don't have to.
Common Questions on Compliant IT Disposal
When you're navigating the ins and outs of IT asset disposal, a few practical questions always seem to pop up for Georgia businesses. Getting straight answers is the key to building a program that’s not just compliant, but one you can be confident in. Let's tackle some of the most common questions we hear, reinforcing the core ideas behind secure and responsible ITAD.
Are We Still Liable After an ITAD Company Takes Our Equipment?
Yes, absolutely—and this is a critical point. Your liability doesn't vanish the moment the truck drives away. It only ends when that liability is formally and legally transferred to your disposal partner.
This is exactly why partnering with a certified vendor who provides a detailed Certificate of Data Destruction is non-negotiable. That certificate, complete with serial numbers and the specific destruction methods used, is your legal proof of due diligence. It’s the document that officially shifts all responsibility for that data from your shoulders to theirs, closing the liability loop and shielding you from any downstream risk. Without it, you’re still on the hook.
What Is the Difference Between R2v3 and e-Stewards Certifications?
Think of R2v3 and e-Stewards as two of the most respected, top-tier credentials in the world of electronics recycling and data security. While both are excellent, they have slightly different philosophies.
- R2v3 (Responsible Recycling) is an incredibly comprehensive standard. It looks at the entire ITAD process, covering everything from environmental protection and employee health and safety to robust data security protocols.
- e-Stewards is often seen as the most stringent standard, particularly because of its absolute ban on exporting hazardous e-waste to developing countries.
Bottom line: A vendor holding either of these certifications has proven they operate at the industry's highest level. Seeing one of these logos is a clear sign you’re dealing with a trustworthy partner capable of managing compliant IT disposal in Georgia.
Is Wiping a Hard Drive as Secure as Physically Destroying It?
For the vast majority of business data, the answer is yes. A multi-pass data wipe that follows the rigorous NIST 800-88 guidelines is a completely secure and compliant way to sanitize a drive. This isn't just deleting files; it's a process that overwrites every single sector, making the original data unrecoverable. The big plus here is that wiping preserves the hardware, allowing the drive—and the computer it's in—to be refurbished and resold, which can bring some value back to you.
However, some situations demand an absolute guarantee. For extremely sensitive information—like proprietary research, classified government data, or simply to comply with a strict internal policy—physical destruction (shredding) is the ultimate solution. It makes data recovery physically impossible because the media is obliterated. A true ITAD partner will consult with you on your specific data sensitivity and offer both certified options to meet your security needs.
Contact Beyond Surplus for certified electronics recycling and secure IT asset disposal. Learn more about our services at https://www.beyondsurplus.com.



