If your Alabama business has a closet full of retired laptops, servers, and monitors, you're not just looking at old hardware—you're looking at a significant risk and a hidden opportunity. This is where professional Alabama ITAD services come in, transforming that potential liability into a secure, compliant, and even profitable part of your business operations. An IT Asset Disposition (ITAD) plan is a strategic approach for decommissioning technology, not just a simple disposal service.
Why a Modern ITAD Strategy is Essential for Alabama Businesses
In today's business environment, simply disposing of old electronics is no longer an option. Every retired hard drive, server, or company smartphone contains a history of sensitive corporate or customer data. For companies in Alabama's tech-forward cities like Huntsville or business hubs like Birmingham, one misstep in the disposal process can lead to devastating data breaches, steep regulatory fines, and lasting damage to your brand's reputation.
A modern ITAD strategy addresses this challenge directly. It should be viewed not as a removal service but as a comprehensive end-of-life plan for your company's technology assets. A robust ITAD program is built on three core pillars designed to protect your organization from every angle.
The Core Pillars of ITAD
A comprehensive ITAD strategy is far more than just recycling. It is a multi-faceted approach designed to safeguard your business interests long after a device is taken offline. Here’s what that means for your commercial operations:
-
Ironclad Data Destruction: This is the most critical component. It ensures that all confidential company, employee, and customer data is permanently and verifiably destroyed using methods that meet strict industry standards like NIST 800-88.
-
Intelligent Value Recovery: Many retired IT assets still hold significant market value. A skilled ITAD partner can securely test, refurbish, and remarket this equipment, turning a potential disposal cost into a revenue stream for your business.
-
Responsible E-Waste Recycling: For any assets with no remaining resale value, responsible electronics recycling is paramount. This pillar ensures that hazardous materials are handled in compliance with environmental regulations and valuable commodities are recovered, all while adhering to a strict zero-landfill policy.
Effectively managing these three areas is what differentiates a basic disposal service from a true, strategic ITAD partner. The objective is to create a seamless, documented process that eliminates risk and maximizes your financial return. You can get a deeper look at the complete process in our detailed guide on what IT Asset Disposition is and how it functions for businesses.
Ultimately, a professional ITAD program is an investment in security, compliance, and financial prudence. It provides a secure chain of custody from the moment equipment leaves your facility, backed by certified documentation that proves you've met your legal and ethical obligations. This transforms a logistical challenge into a streamlined, secure, and beneficial part of your business operations.
Ensuring Ironclad Data Security and Compliance
For any business in Alabama—particularly those in healthcare, finance, or government contracting—data security is a legal mandate. The single most important function of any Alabama ITAD service is to ensure that the sensitive information on your retired equipment is permanently destroyed, with no possibility of recovery. This process goes far beyond simple file deletion; it requires a meticulous, documented, and verifiable methodology.
Regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the Fair and Accurate Credit Transactions Act (FACTA) impose strict rules for protecting sensitive information. These rules apply directly to the hard drives and storage devices in the servers, laptops, and networking gear your business is decommissioning. A failure to comply can lead to significant financial penalties and a damaged reputation that is difficult to repair.
Understanding Data Destruction Methods
To meet these stringent compliance standards, professional ITAD partners utilize several certified methods to completely sanitize storage media. Each method offers a different level of security, and the appropriate choice depends on the asset type and your organization's specific risk profile.
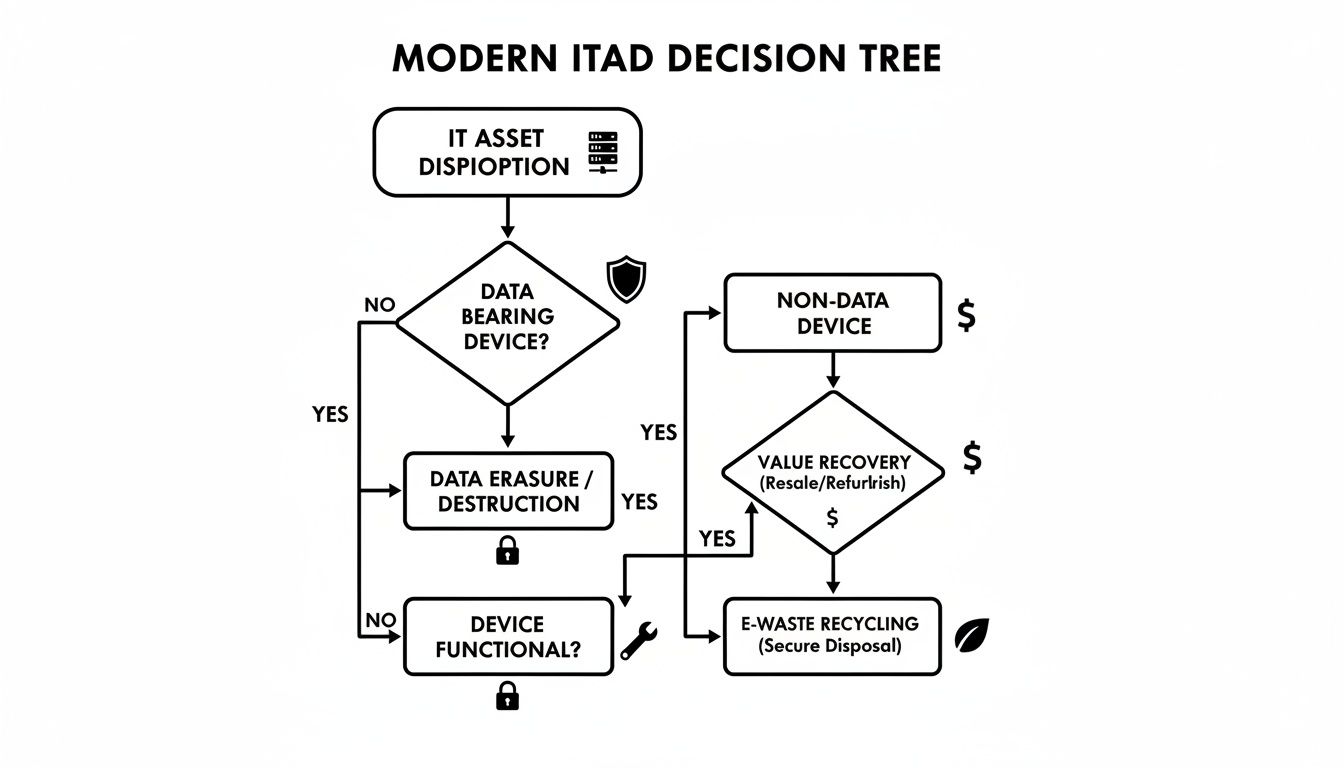
This flowchart illustrates how a professional ITAD strategy prioritizes data security. After data is verifiably destroyed, assets are assessed for potential value recovery before any remaining materials are processed for responsible e-waste recycling.
To provide a clearer understanding, here is a breakdown of the most common data destruction methods for commercial assets.
Comparing Data Destruction Methods for Your Business
This table compares the three primary methods of data destruction, helping Alabama IT managers choose the right option based on security needs, asset type, and compliance requirements.
| Method | Description | Best For | Compliance Level | Value Recovery Potential |
|---|---|---|---|---|
| Certified Data Wiping | A software-based process that overwrites a drive with random data, making original information unrecoverable. Follows standards like NIST 800-88. | Newer, functional drives (HDDs & SSDs) that can be refurbished and resold. | High | Highest |
| Degaussing | Uses a powerful magnetic field to instantly scramble the data on magnetic media, rendering the drive unusable. | Older magnetic hard drives (HDDs) and backup tapes requiring fast, total erasure. | Very High | None |
| Physical Shredding | An industrial shredder grinds storage devices into small, unrecognizable pieces, guaranteeing data can never be accessed again. | End-of-life drives, SSDs, or devices with the highest security requirements. | Absolute | None |
Choosing the right method is a strategic decision. If recovering capital from your retired equipment is a priority, certified data wiping is the optimal choice. However, if the sole objective is absolute, irreversible data destruction, physical shredding provides the ultimate security.
The Importance of Chain of Custody
How can you prove your devices were handled securely from your facility to their final disposition? This is accomplished through a secure chain of custody—a documented, chronological trail that tracks every asset from your location to its final processing.
This meticulous tracking, often using serialized asset tags and secure, GPS-monitored transport, creates an unbreakable audit trail. It’s the verifiable proof you need for both internal governance and any regulatory audits that come your way.
This level of accountability is increasingly critical. The North America IT Asset Disposition market is projected to grow from USD 4.85 billion in 2025 to USD 6.59 billion by 2030, driven largely by these precise compliance and security demands. With the average cost of a data breach reaching USD 4.45 million, partnering with a certified ITAD vendor is now a core component of risk management for businesses of all sizes.
It is also important to consider less obvious devices. Equipment like printers and copiers can store sensitive data on internal memory. A thorough ITAD process includes protecting print data on devices to ensure no information is left behind.
The final element is the Certificate of Data Destruction. This official document serves as your definitive proof of compliance. It lists the unique serial numbers of the sanitized devices and confirms the date and method of destruction. You can learn more in our complete guide to the Certificate of Destruction for hard drives. This is not merely a receipt; it is your legally defensible record that your organization has fulfilled its due diligence.
Turning Old Tech Into New Revenue Streams
Most companies view retired IT equipment as a sunk cost—a logistical burden that must be managed securely. However, that aging hardware can actually be a hidden revenue stream. This is the core principle behind value recovery, a key component of modern Alabama ITAD services that transforms asset disposal from a necessary expense into a financial opportunity.
Instead of shredding every piece of equipment, a strategic ITAD partner evaluates your assets for remarketing potential. Your used laptops, servers, networking gear, and other enterprise hardware may still have a valuable second life. This is not simply selling off old tech; it is a calculated strategy to maximize the return on your original technology investment.

The Asset Remarketing Process
A skilled ITAD partner employs a meticulous process to unlock the value in your retired equipment, beginning the moment your assets arrive at their secure facility.
First, each item is inventoried, and its condition is carefully assessed. Technicians test its functionality, document any cosmetic wear, and identify key specifications like processor speed, RAM, and storage capacity. This initial audit determines if an asset is a viable candidate for refurbishment.
After performing certified data destruction to NIST 800-88 standards, the refurbishment process begins. This may involve:
- Cleaning and cosmetic repairs to improve the device's appearance.
- Component upgrades, such as adding more RAM or installing a larger solid-state drive (SSD).
- Thorough diagnostic testing to ensure all parts are fully functional.
Once a device is fully refurbished, it is ready for the secondary market. A professional partner leverages a global network of buyers to find the ideal market for each asset, ensuring you receive the highest possible return.
Realizing Financial Returns
For Alabama companies, this process can generate a significant financial return. The revenue from remarketed assets can offset—or even completely cover—the costs of data destruction and recycling for equipment that could not be resold. In many cases, it can result in a net profit.
This transforms your secure disposal program from a line item on your expense budget into an operation that’s self-funding or even profitable. It’s a smart financial move that also supports a circular economy.
The global IT Asset Disposition market is expanding rapidly, demonstrating the immense potential in reuse and remarketing. The industry was valued at USD 15.58 billion in 2023 and is projected to more than double to USD 32.36 billion by 2032. This growth is overwhelmingly driven by the value recovery sector, positioning Alabama ITAD providers as key players in a sustainable and financially sound global ecosystem.
By partnering with an expert, you can fully capitalize on this opportunity. Beyond Surplus offers comprehensive IT equipment buy back services, providing fair market value for your retired technology. This approach ensures your business not only meets its security and compliance obligations but also maximizes the financial value remaining in its assets.
Navigating E-Waste and Environmental Responsibility
After data has been destroyed and any reusable equipment has been remarketed, what happens to the remaining assets? For businesses in Alabama, this is where corporate social responsibility intersects with stringent environmental regulations. Managing electronic waste, or e-waste, is not just an environmental initiative; it is essential for protecting your brand and ensuring legal compliance. Retired technology cannot be disposed of with general office waste and must be kept out of landfills.
Most electronics contain hazardous materials that can cause significant environmental damage. A retired server, monitor, or PC may contain substances like lead, mercury, cadmium, and brominated flame retardants. If these materials leach into the soil and groundwater from a landfill, they can create a serious ecological hazard. Federal and state regulations exist to hold businesses accountable for the proper disposal of their electronics.
The De-Manufacturing Process
Assets with no resale value enter a highly controlled de-manufacturing process. This is not simply crushing old equipment; it is a careful, step-by-step disassembly designed to recover raw materials for reuse.
This process functions like a reverse assembly line. Trained technicians disassemble each device, separating it into its core components:
- Hazardous Material Removal: Any hazardous elements, such as mercury lamps from flat-screen monitors or old batteries, are safely removed and contained.
- Component Sorting: Circuit boards, power supplies, memory modules, and other internal parts are sorted based on their type and material composition.
- Material Segregation: The remaining materials are separated into clean commodity streams, such as steel, aluminum, plastic, and glass.
Once sorted, these raw materials are shredded, baled, and transported to specialized smelters and refiners. From there, they re-enter the manufacturing supply chain to create new products. This circular approach prevents toxic materials from entering the environment and reduces the need to mine for new resources, saving energy and protecting natural habitats.
The Critical Role of Certifications
How can you be certain that your Alabama ITAD services provider is handling this process correctly? The proof lies in their certifications. For any business concerned with its reputation, partnering with a vendor holding top-tier industry certifications is non-negotiable. These credentials are hard-earned proof of a commitment to the highest industry standards.
The two most important certifications to look for are:
- R2 (Responsible Recycling): This standard confirms that a recycler adheres to best practices for environmental safety, data security, and the health and safety of their workers and the community.
- e-Stewards: This is another globally respected standard that holds recyclers to a strict zero-landfill and zero-export policy for hazardous e-waste.
A certified partner provides a documented, transparent chain of custody for all your e-waste. This is your guarantee that your company’s name will never be associated with irresponsible dumping in local landfills or overseas, protecting you from fines and negative publicity.
By choosing a certified recycler, you ensure every component of your retired IT equipment is managed ethically and sustainably. This reflects positively on your organization and demonstrates a serious commitment to modern corporate environmental stewardship. Understanding the benefits of recycling e-waste is a strategic step for any forward-thinking Alabama business aiming to reduce its environmental footprint and meet its compliance obligations.
Streamlining Your ITAD Logistics and Operations
A robust ITAD strategy is defined by more than just data destruction and recycling—it requires flawless execution. How does a pallet of retired servers travel from your office in Montgomery or a data center in Huntsville to a secure processing facility without a single security gap? The answer is professional, detail-oriented logistics, a core component of any reliable Alabama ITAD service.
The process begins when you schedule a pickup. A true ITAD partner dispatches trained, insured technicians in secure, often GPS-tracked vehicles to manage the on-site removal. This ensures that from the moment your assets leave your control, they are under constant, documented supervision.

Establishing an Unbreakable Chain of Custody
This meticulous approach is the foundation of a secure chain of custody. It creates an unbreakable evidence trail for your IT equipment. Upon arrival at your location, technicians begin the critical work of inventorying and asset-tagging every device designated for disposal.
Each laptop, server, hard drive, and network switch is assigned a unique serial number or barcode. This identifier is scanned and logged, creating an initial manifest that you can verify and sign before any equipment leaves your premises. This step is non-negotiable, as it establishes the baseline for all subsequent tracking and reporting.
This on-site, serialized inventory is your first layer of defense. It eliminates the risk of assets going missing in transit and provides a clear, documented record of exactly what was handed over, and to whom.
This level of detail is the hallmark of a premier provider. It transforms a potentially chaotic process into a predictable and secure operation, providing the peace of mind that comes with complete transparency. For complex projects, you can learn more about how a professional partner manages these intricate logistics with nationwide reverse logistics services.
The Power of Detailed Documentation
Once your assets are securely transported to the ITAD facility, the documentation process continues. The initial on-site manifest is reconciled against the equipment received, confirming that everything has arrived safely and is accounted for. From this point, every action taken—from data destruction to recycling—is recorded against the asset’s unique serial number.
This creates a comprehensive audit trail that follows each device through its entire end-of-life journey. The documentation you receive from a top-tier partner will typically include:
- Serialized Inventory Reports: A detailed list of every asset processed, including make, model, and serial number.
- Chain-of-Custody Forms: Signed and dated records tracking the transfer of assets from your business to the ITAD provider and within their facility.
- Certificates of Data Destruction and Recycling: Legally binding documents that serve as your official proof of compliance, confirming that data was irretrievably destroyed and e-waste was handled responsibly.
This collection of documents is more than just paperwork; it is your definitive proof of due diligence. Whether for internal governance, stakeholder reporting, or responding to a regulatory audit, this verifiable trail demonstrates that your organization took every necessary step to protect its data and meet its environmental obligations. It makes the entire ITAD process seamless, transparent, and worry-free.
How to Choose the Right Alabama ITAD Partner
Selecting the right partner for your Alabama ITAD services is a critical business decision. It directly impacts your company’s data security, financial returns on retired assets, and public reputation. This is not comparable to hiring a standard disposal service; you are entrusting a vendor with devices containing your most sensitive information.
While a general junk removal company is suitable for clearing out old office furniture, ITAD requires specialized expertise. The stakes are too high for a non-specialist. You need a certified, transparent, and secure provider, and a thorough vetting process is your best defense against a potential data breach or compliance violation.
Key Certifications to Demand
Certifications are not merely marketing tools; they are hard-earned credentials proving a vendor adheres to the strictest industry standards for data security and environmental responsibility. They serve as a third-party validation of a provider's processes.
Before engaging a vendor, ensure they can provide proof of these critical certifications:
- R2 (Responsible Recycling): This certification ensures the vendor follows best practices for electronics recycling, data security, and worker safety. It is a global standard for responsible e-waste management.
- NAID AAA Certification: This is the gold standard for data destruction. A NAID AAA certified company has undergone rigorous third-party audits of its data wiping and shredding processes, from hiring practices to facility security.
The absence of these certifications is a significant red flag, indicating that a potential partner may lack the validated processes required to protect your business. Always request their certification numbers for independent verification.
Questions to Ask Potential Vendors
Once you have confirmed their credentials, delve into the details of their operations. A reputable ITAD partner will provide clear, direct answers to the following questions.
Your goal is to find a partner who sees themselves as an extension of your security and compliance team, not just a pickup service. Transparency is the hallmark of a trustworthy ITAD provider.
Use this checklist to guide your discussions:
- Data Security: "What data destruction methods do you offer, and can you confirm they meet NIST 800-88 standards?"
- Chain of Custody: "Walk me through your chain-of-custody process. What happens from the moment my assets leave my building?"
- Logistics: "Are your trucks secure and tracked with GPS? Are your drivers insured and background-checked?"
- Reporting: "What type of documentation will I receive? Will it include serialized reports and official Certificates of Data Destruction?"
- Insurance: "What types of insurance policies do you carry? Specifically, do you have coverage for data breaches and pollution liability?"
- Downstream Vetting: "How do you audit your downstream recycling partners to guarantee a zero-landfill policy?"
The demand for these specialized services is growing. In the United States, the IT Asset Disposition market reached USD 6.0 billion in 2024, largely driven by rising cyber threats and the constant need for businesses to upgrade technology. Since remarketing can often recover 20-30% of an asset's original value, finding a partner who is an expert in both security and value recovery is essential. You can explore more insights about the ITAD market growth on imarcgroup.com.
Answering Your ITAD Questions
When it comes to IT Asset Disposition, it is natural for Alabama businesses to have questions. Here are answers to some of the most common inquiries to provide a clearer understanding of how a professional ITAD program operates and why it is essential.
What Kind of Equipment Can You Take?
A professional Alabama ITAD service can manage nearly any piece of business technology. This includes standard office equipment like laptops, desktops, monitors, and printers, as well as enterprise-grade hardware.
Our services cover:
- Servers and server racks
- Networking equipment such as switches, firewalls, and routers
- Data storage arrays and SANs
We also handle specialized equipment from healthcare, manufacturing, and laboratory environments. A qualified ITAD partner will assess every asset to determine the optimal disposition path—whether that is secure data destruction, refurbishment for resale, or responsible recycling.
Is My Business Too Small for This?
No. A common misconception is that ITAD services are only for large corporations with high volumes of equipment. In reality, these services are scalable and equally critical for small and medium-sized businesses (SMEs) in Alabama.
Many believe ITAD is an enterprise-only service, but SMEs handle sensitive data and face the same compliance risks. Secure disposal is a necessity for any business, regardless of size.
In fact, smaller businesses can be more vulnerable to the financial and reputational damage of a data breach resulting from improper disposal. A reputable ITAD provider will offer flexible solutions, such as scheduled pickups or drop-off services, making it easy for smaller organizations to achieve the same level of security and compliance as larger enterprises.
How Can I Be Sure My Data Is Really Gone?
This is the most critical question, and a certified ITAD partner provides multiple layers of verification. First, they use data sanitization methods that comply with government and industry standards, such as those from the Department of Defense (DoD 5220.22-M) and the National Institute of Standards and Technology (NIST SP 800-88).
Second, the entire process is tracked. A secure chain of custody follows every device from your facility to its final disposition, eliminating gaps in security.
Finally, upon completion, you will receive a Certificate of Data Destruction. This legally binding document serves as your official proof that the data on your assets has been permanently destroyed. It is an essential record for compliance audits and internal governance.
Ready for a partner that delivers certified, secure, and profitable Alabama ITAD services for your business? Contact Beyond Surplus today for a consultation to learn how we can help you manage your end-of-life IT assets. Find out more at https://www.beyondsurplus.com.



