For any business in Arkansas, protecting sensitive data isn't just a good practice—it's an operational necessity. While software-based wiping is often discussed, when it comes to guaranteeing that proprietary, customer, or regulated data is permanently unrecoverable, physical destruction through professional hard drive shredding is the only 100% foolproof method. This process ensures your company's information can never be compromised after IT assets are retired.
Why Shredding Is the Gold Standard for Data Destruction

Consider the sensitive files on your company’s servers and laptops. "Deleting" a file or reformatting a drive is like wiping a whiteboard—to the casual observer, it appears empty. However, faint traces and ghost images of the original data often remain. With commercially available data recovery software, a determined individual could easily reconstruct what was previously stored. This is a significant risk for any Arkansas business handling confidential information.
Hard drive shredding, in contrast, is like feeding that same whiteboard into an industrial metal shredder. The media isn't just erased; the physical drive is annihilated into thousands of tiny, unrecognizable fragments. Reassembling the data is physically impossible. This complete and irreversible destruction is why it's the gold standard for secure IT asset disposal.
The Unseen Risks of Improper Disposal for Businesses
For an Arkansas business, the consequences of improper data destruction are severe. The risks extend far beyond a simple data leak—they can threaten your company's financial stability, its market reputation, and its legal standing.
Here’s what is at stake:
- Data Breaches and Severe Fines: A single discarded hard drive could expose thousands of client records, internal financials, or trade secrets. Such a lapse can lead to crippling penalties under federal laws like HIPAA for healthcare data or GLBA for financial information.
- Reputational Damage: News of a data breach can shatter customer trust and brand credibility. Rebuilding that trust is often far more costly and difficult than paying a regulatory fine.
- Loss of Intellectual Property: Your company's most valuable assets are often digital. Insecure disposal is equivalent to handing your competition your product designs, strategic plans, and customer databases.
Why Physical Destruction Is a Non-Negotiable Security Control
When IT assets reach their end-of-life, especially those that stored sensitive data, physical destruction is the only method that eliminates all doubt. Software wipes can fail due to bad sectors on a drive, human error, or incompatibility with newer Solid-State Drives (SSDs). Shredding bypasses all these potential points of failure, delivering a guaranteed outcome every time.
The National Institute of Standards and Technology (NIST) confirms this in its Special Publication 800-88, the benchmark for data disposal. NIST identifies physical destruction as the most secure method for media sanitization. When regulatory bodies and security experts endorse a method as the ultimate safeguard, businesses should take note.
By choosing certified Arkansas hard drive shredding, you are not just disposing of old equipment. You are actively defending your business against a significant operational and financial risk. It is the final, definitive step to ensure your confidential information remains confidential—permanently. To learn more about how this process guarantees compliance and total peace of mind, explore Beyond Surplus's certified hard drive destruction services.
Navigating Data Destruction Compliance in Arkansas
For businesses operating in Arkansas, understanding data security laws is a fundamental aspect of risk management. While there may not be a specific state law dictating how to dispose of an old hard drive, your company is still subject to powerful federal regulations that mandate the secure destruction of sensitive information.
These federal laws establish a non-negotiable baseline for data protection. Failing to comply can result in severe legal and financial consequences. That's why professional Arkansas hard drive shredding isn't merely a best practice; it's a critical component of your legal and cybersecurity defense strategy.
Federal Regulations Impacting Arkansas Businesses
Even without a specific state e-waste mandate, Arkansas businesses are held to the same high standards as companies nationwide when it comes to protecting consumer and patient data. Compliance is determined by the type of information you handle, not your physical location.
Key federal laws include:
- HIPAA (Health Insurance Portability and Accountability Act): Any organization handling patient data must adhere to the HIPAA Security Rule, which requires protecting electronic Protected Health Information (ePHI) from its creation to its secure and permanent destruction.
- GLBA (Gramm-Leach-Bliley Act): This applies to financial institutions like banks, investment firms, and insurance companies. The GLBA Safeguards Rule mandates the protection of customers' private financial information, including its secure disposal.
- FTC Disposal Rule: This rule applies to nearly any business that handles consumer credit information. It legally requires you to dispose of this data in a manner that prevents it from being reconstructed, making physical destruction an ideal compliance solution.
Failure to meet these standards can lead to substantial fines, litigation, and damage to your company's reputation.
State-Level Requirements and Best Practices
While Arkansas does not have explicit statewide e-waste recycling mandates, businesses are still required to protect personal information and report data breaches. This reality makes NAID AAA certified physical destruction the de facto standard for security-conscious companies.
The most effective way to manage risk is to adhere to the NIST SP 800-88 guidelines for media sanitization. When a storage device reaches its end-of-life, especially one that held sensitive data, shredding or pulverization is the only way to be 100% certain the data is unrecoverable and to provide a strong defense against regulatory scrutiny. A compliant process should always include serialized asset tracking and a formal Certificate of Destruction.
Your Legal Proof: The Certificate of Destruction
How can you prove that you properly destroyed sensitive data long after the hard drives have been turned into fragments? The answer is the Certificate of Destruction. This document is more than a receipt; it is your official legal evidence of compliance.
A Certificate of Destruction is your auditable proof that you fulfilled your duty to protect sensitive data. It formally documents the process, including asset serial numbers, date, and method of destruction, effectively transferring liability from your organization to your certified disposal partner.
This certificate is your primary defense in an audit or legal challenge. It will always include:
- The date and method of destruction.
- A serialized list of all destroyed assets.
- A clear statement confirming the data is unrecoverable.
- The signature of an authorized representative from the destruction company.
This paper trail demonstrates due diligence and responsible data stewardship. For a complete strategy on managing end-of-life IT assets, our guide to Arkansas electronics recycling ensures your entire disposal plan is secure and compliant.
On-Site vs. Off-Site Hard Drive Shredding for Arkansas Businesses
After deciding to physically destroy your obsolete hard drives, the next critical decision is where the destruction will occur. For businesses in Arkansas, the choice is between on-site (mobile) shredding and off-site shredding at a secure facility. Both methods achieve the same result—complete data destruction—but offer different advantages based on your company's security protocols, budget, and logistical needs.
On-Site Shredding: The Ultimate in Visual Verification
On-site shredding, also known as mobile shredding, brings the destruction process directly to your business location. A specialized truck equipped with an industrial-grade shredder arrives at your Arkansas facility. Your hard drives are scanned, logged, and then destroyed right in front of you.
This method offers unparalleled transparency and control. For organizations handling highly sensitive data or operating under strict compliance frameworks like HIPAA, witnessing the destruction provides an unmatched level of assurance.
Key benefits of on-site shredding include:
- Maximum Security: The chain of custody is minimal. Drives go directly from your facility into the shredder, eliminating any transportation risk.
- Immediate Verification: You can physically watch each drive being destroyed, providing instant confirmation of a job done correctly.
- Compliance Peace of Mind: Witnessing and documenting the destruction process simplifies audit trails and demonstrates the highest level of due diligence.
Off-Site Shredding: A Cost-Effective and Scalable Solution
Off-site shredding provides the same certified, permanent destruction, but the process takes place at a dedicated, secure facility. A vetted technician visits your Arkansas office to securely pack your hard drives into locked, tamper-evident containers. These containers are then transported in a GPS-tracked, secure vehicle to a specialized shredding plant. Upon arrival, the drives are inventoried and destroyed under continuous video surveillance, with the entire process meticulously documented to maintain an auditable chain of custody.
The advantages of off-site shredding are compelling:
- Cost-Effectiveness: By processing drives from multiple clients in large, efficient batches, vendors can offer off-site services at a more competitive price point, especially for large-scale projects.
- Scalability: Secure facilities are designed to handle massive volumes, making off-site shredding the ideal solution for data center decommissioning or large corporate IT asset refreshes.
- Minimal Business Disruption: The pickup process is quick and efficient, requiring minimal time from your staff and causing no operational disturbance at your workplace.
The decision often comes down to a trade-off: on-site shredding prioritizes direct, visual verification for maximum assurance, while off-site shredding prioritizes cost-efficiency and scalability without compromising certified security.
Comparing On-Site and Off-Site Hard Drive Shredding
| Feature | On-Site Shredding | Off-Site Shredding |
|---|---|---|
| Location | At your Arkansas facility | At a secure, specialized plant |
| Verification | Direct, visual confirmation | Documented and video-recorded |
| Chain of Custody | Assets never leave your site | Secure, GPS-tracked transport |
| Best For | Maximum security, compliance | Large volumes, budget optimization |
Ultimately, whether you choose on-site or off-site, partnering with a certified vendor ensures the same critical outcome: your data is permanently destroyed and completely unrecoverable. To determine the best method for your company's security policies and budget, review a detailed breakdown of certified hard drive destruction services.
The Importance of Certification and Chain of Custody
When you entrust a vendor with your company's retired hard drives, how can you be certain that every single device is properly destroyed? While trust is important, in the world of data security, verifiable proof is essential. This is where two core concepts provide your guarantee: third-party certification and an unbroken chain of custody. These are the pillars of a defensible data destruction program.
A premier certification like NAID AAA represents a rigorous, independent audit of a data destruction vendor's entire operation. To earn and maintain this certification, a provider must demonstrate the highest standards for facility security, employee screening, and documented procedures. It is a validation that their process—from pickup at your Arkansas office to the final recycling of shredded materials—is designed to protect your interests.
What NAID AAA Certification Guarantees
Choosing a NAID AAA certified partner for your Arkansas hard drive shredding means you are engaging a vendor whose security protocols have been thoroughly vetted.
This certification confirms:
- Secure Facilities: The plant has strict access controls and 24/7 surveillance.
- Vetted Employees: All personnel with access to your assets have passed extensive background checks.
- Operational Integrity: Shredders and processes are regularly audited to ensure they meet industry standards for complete data destruction.
- Insurance Requirements: The provider carries specific insurance to protect you from liability in the unlikely event of a data breach.
The Unbroken Chain of Custody
While certification validates the vendor, the chain of custody validates the process for your specific project. It is a meticulous, step-by-step documentation trail that tracks your assets from your possession to their final destruction. This unbroken record serves as your legal proof of proper disposal.
The process is designed to eliminate any gaps where a drive could be misplaced or compromised. This workflow illustrates how it works, from your facility to the final, documented shred.
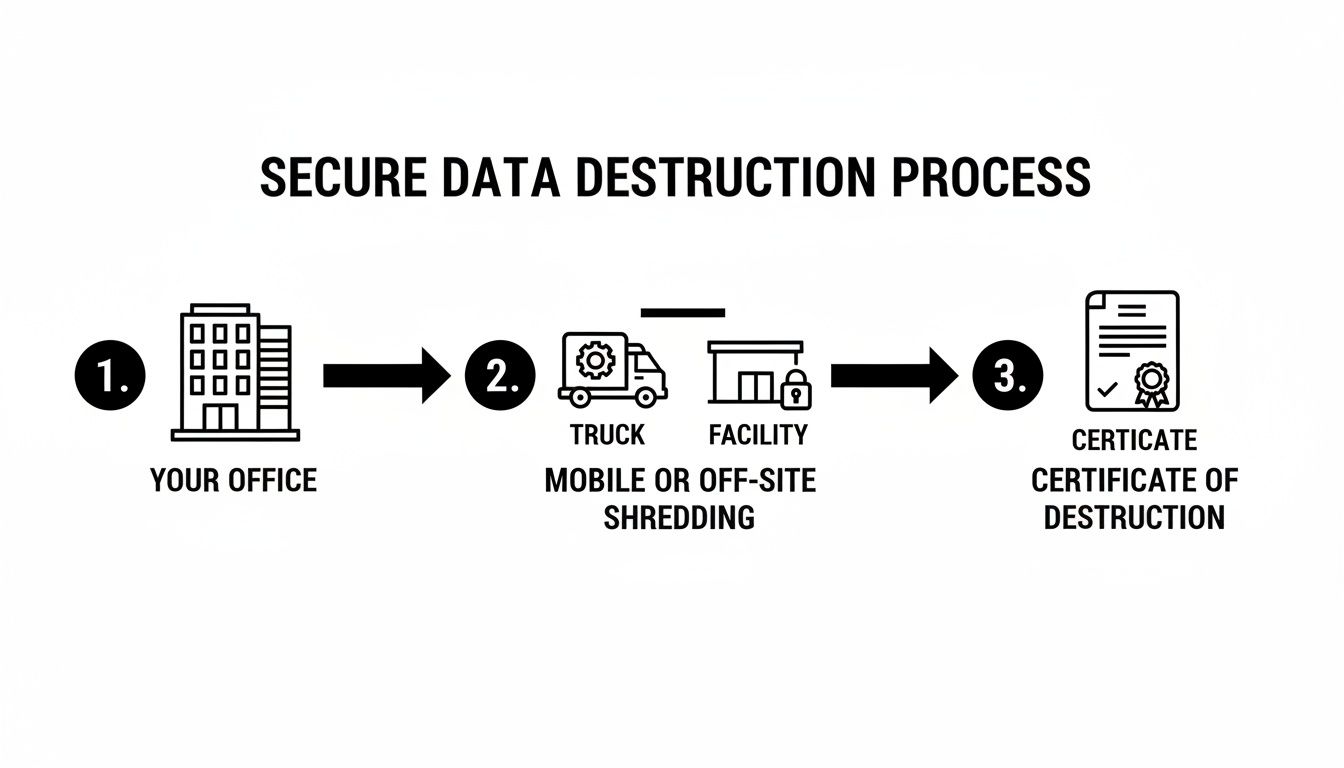
This visual highlights the critical handoffs in a secure workflow. The objective is to account for every asset until it is physically destroyed and documented.
Here is the process:
- Serialized Scanning: A technician scans the unique serial number or asset tag of every drive at your location, creating an initial inventory that forms the basis of the audit trail.
- Secure Transport: Drives are placed in locked, tamper-evident containers and transported in a secure, GPS-tracked vehicle.
- Verified Destruction: Whether on-site or at a secure plant, the drives are shredded, and the process is documented, often with video surveillance.
- Certificate of Destruction: You receive a formal document listing every serial number, confirming that each asset was completely destroyed.
A robust chain of custody is non-negotiable. It transfers liability for the data from your business to your certified destruction partner, providing a defensible, auditable record that withstands regulatory scrutiny.
This final document is your ultimate proof of compliance. To understand its legal significance, learn more about what a proper Certificate of Destruction entails and why it is a critical component of your risk management strategy.
Securing Every Device: A Strategy Beyond Hard Drives

In a modern Arkansas business, sensitive data is not confined to the traditional hard disk drives (HDDs) in servers and desktops. It is distributed across a wide ecosystem of devices, each representing a potential security risk if not managed properly at end-of-life. A comprehensive data destruction policy must address all data-bearing assets. Focusing only on HDDs is like locking your office's front door while leaving the windows open. To effectively mitigate risk, your strategy for Arkansas hard drive shredding must be expanded to include all forms of electronic storage media.
Why Shredding Is Essential for Modern Media Types
Legacy methods for sanitizing traditional HDDs, such as wiping or degaussing, can be ineffective on modern storage technology, particularly Solid-State Drives (SSDs). An HDD stores data magnetically on a spinning platter, which can be overwritten by software or scrambled by a powerful magnetic field (degaussing).
SSDs, however, use flash memory chips and complex wear-leveling algorithms that distribute data across the drive to extend its lifespan. This architecture makes it nearly impossible for software to guarantee that all data has been overwritten. Furthermore, degaussing is completely ineffective against an SSD's non-magnetic flash memory. This makes physical destruction the only reliable solution.
For SSDs, flash drives, and other flash-based media, physical destruction is the only sanitization method recognized by the National Institute of Standards and Technology (NIST) as 100% effective. It bypasses the technical limitations of other methods, ensuring data is irrecoverable.
Expanding Your Data Destruction Checklist for Full Compliance
A comprehensive data security plan must identify and secure every device that could contain proprietary or regulated information. Consider all the technology your Arkansas business utilizes daily.
Your asset destruction checklist should include:
- Solid-State Drives (SSDs): Found in most modern laptops, desktops, and servers. They must be physically shredded.
- Backup Tapes: LTO, DLT, and other formats can hold years of archived company data, making them a high-value target.
- USB Flash Drives: These small, easily lost devices can contain a significant amount of sensitive information.
- Smartphones and Tablets: These devices are repositories of data, from emails and contacts to company network credentials.
- Optical Media: CDs, DVDs, and Blu-ray discs used for software distribution or data archiving must also be destroyed.
By implementing a policy that mandates the physical destruction of all these items, you transform a basic hard drive disposal plan into a complete, defensible data security strategy. This proactive approach ensures no device leaves your control without its data being rendered permanently unreadable.
Selecting the Right Secure ITAD Partner in Arkansas
Choosing a vendor for end-of-life IT asset management is a critical business decision. The wrong choice can lead to significant consequences, from regulatory fines to irreversible brand damage. For businesses in Arkansas, selecting the right secure ITAD partner is about finding a provider who functions as an extension of your security team. This requires asking tough questions and demanding verifiable proof of their security protocols. A top-tier provider won't just claim to be secure; they will demonstrate it through certifications, transparent processes, and audit-ready documentation.
Core Questions to Ask Any Potential Vendor
Before signing a contract, your due diligence should focus on several non-negotiable areas. The responses you receive will quickly distinguish professional, certified providers from the rest.
Begin with these essential questions:
- Are You NAID AAA Certified? This is the gold standard for secure data destruction. NAID AAA certification is not a one-time achievement; it involves ongoing, unannounced audits that verify a vendor’s security controls, hiring practices, and operational integrity.
- Can You Provide a Detailed Chain of Custody? Ask them to explain their entire process, from serialized asset scanning at your office to the final Certificate of Destruction. An unbroken chain of custody is your legal proof of due diligence.
- What Does Your Downstream Data Liability Insurance Cover? A reputable partner will carry specialized insurance designed to protect you in the unlikely event of a data breach. This demonstrates their commitment and provides an additional layer of financial protection.
Beyond Security: Ensuring Environmental Responsibility
A true ITAD partner understands that their responsibility extends beyond data destruction. The shredded materials—primarily aluminum, plastics, and circuit boards—must be managed in an environmentally responsible manner.
Ask potential vendors about their recycling policies and certifications like R2 or e-Stewards. These credentials provide assurance that all e-waste is processed in compliance with environmental regulations, preventing hazardous materials from entering landfills. This aligns your data security program with corporate social responsibility goals and is a hallmark of a professional operation.
The global hard drive destruction market is projected to grow from USD 1.65 billion in 2024 to over USD 5.05 billion by 2035, driven by tightening data privacy regulations. For Arkansas businesses, this trend highlights the importance of partnering with certified vendors who can deliver fully documented, auditable destruction services that meet any compliance challenge.
A partner’s commitment to providing a transparent, auditable process is the ultimate measure of their reliability. This is about more than destroying hardware; it's about providing the peace of mind that comes from knowing your data is irretrievably destroyed and your legal obligations have been met.
Understanding a partner’s full capabilities, including their hard drive data recovery expertise, can also inform a more complete data management strategy. By choosing a partner who provides certified, professional services, any business in Arkansas can secure its data with confidence. To see how Beyond Surplus meets these rigorous standards, explore our comprehensive Arkansas ITAD services.
Answers to Your Top Hard Drive Shredding Questions
As Arkansas businesses retire IT equipment, critical questions arise about data protection. Making an informed decision is vital, so here are answers to the most common concerns regarding professional hard drive shredding.
Is Wiping My Hard Drives Sufficient, or Is Shredding Necessary?
Data wiping can be appropriate for drives intended for reuse within your organization. However, for any drive at its end-of-life, wiping is insufficient. Software can fail on drives with bad sectors and is often unreliable on Solid-State Drives (SSDs) due to their data storage architecture. For drives containing sensitive information, physical shredding is the only method that guarantees the data is 100% irrecoverable. For Arkansas businesses subject to regulations like HIPAA or the FTC Disposal Rule, certified shredding provides an ironclad defense against a potential data breach.
What Exactly Is a Certificate of Destruction?
A Certificate of Destruction is a formal, legal document that serves as official proof that your data-bearing devices were securely and permanently destroyed. It provides a serialized inventory of every asset, detailing the date and method of destruction. This document is your key evidence in an audit, as it formally transfers liability for the data from your organization to your destruction partner, creating a clear and defensible audit trail.
My Business Is Located in a Rural Area of Arkansas. Can I Still Access This Service?
Yes. Proximity to a major city like Little Rock or Fayetteville is not a barrier to receiving top-tier, certified service. Leading IT Asset Disposition (ITAD) companies maintain logistics networks that cover all of Arkansas. This ensures that every business in the state, regardless of location, can access compliant and secure data destruction services. A professional partner will manage all logistics, making the process seamless whether you have a handful of drives or an entire data center to decommission.
What Is the Typical Cost for Hard Drive Shredding in Arkansas?
There is no standard price for Arkansas hard drive shredding, as the cost depends on several factors:
- Volume of drives: The price per drive typically decreases as the quantity increases.
- Service type: On-site shredding (mobile service at your location) is a premium service and costs more than off-site shredding at a secure facility.
- Logistics: The pickup distance and complexity of the project can influence the final price.
Generally, off-site shredding is the most cost-effective option, particularly for larger quantities. The best approach is to request a custom quote from a certified vendor who can tailor the service to your specific needs and budget.
For a comprehensive, certified approach to electronics recycling and secure data destruction, partner with Beyond Surplus. We provide auditable, compliant solutions to protect your business. Get your custom quote today by visiting us at https://www.beyondsurplus.com.



